Other MALWARES Part 13
Most of these malwares try to install themselves and are easily blocked by the "Trojan Generic" procative alert.
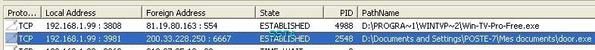
Some malwares only open connections, and are not blocked by the proactive module (F1 results).
Unfortunately, most .jpg has been lost for most of these sample tests.
-BacktoDemon: P1/P2
-Wolf telnEt backdoor (Backdoor.Win32 Wolf.14): P1/P2
-Trojan Downloader DSWeb: P1/P2
-Backdoor AnalFTP: F1/P2
-Backdoor Bushtrommel: P1/P2
-Lame Rat: P1/P2

-Elite Rat: P1/P2
-PsyRat: P1/P2
-NetControl: P1/P2
-SkryptyRat: P1/P2
The malware was not known by Kaspersky lab during the test (2006/08), but the PDM has done its job (trojan generic).
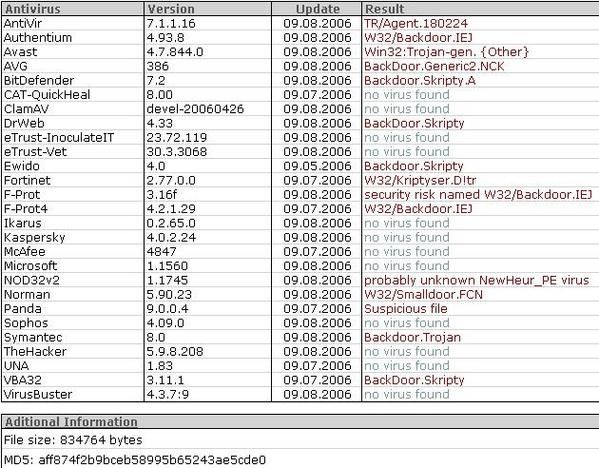
-TequilaBandita (Win32 Banitos): P1/P2
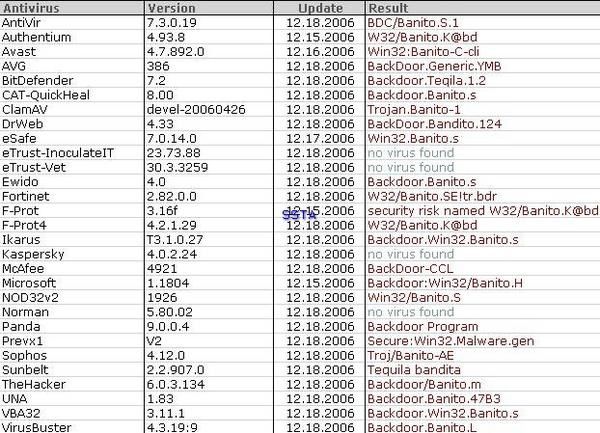
-Trojan INotifier: P1/P2
-ConsoleDevil backdoor: P1/P2
Antivirus Version Update Result
AhnLab-V3 2007.5.31.2 06.01.2007 Win-Trojan/Downloader.10788
AntiVir 7.4.0.29 06.01.2007 TR/Hijack.Explor.273
Authentium 4.93.8 05.23.2007 Possibly a new variant of W32/SecRisk-ProcessPatcher-Sml-based!Maximus
Avast 4.7.997.0 06.01.2007 Win32:Small-APV
AVG 7.5.0.467 06.01.2007 BackDoor.Generic3.CKI
BitDefender 7.2 06.02.2007 Backdoor.Small.CP
CAT-QuickHeal 9.00 06.01.2007 no virus found
ClamAV devel-20070416 06.02.2007 Trojan.Small-272
DrWeb 4.33 06.02.2007 BackDoor.Chaos
eSafe 7.0.15.0 05.31.2007 Win32.Small.mg
eTrust-Vet 30.7.3684 06.02.2007 no virus found
Ewido 4.0 06.02.2007 Backdoor.Small.mg
FileAdvisor 1 06.02.2007 no virus found
Fortinet 2.85.0.0 06.02.2007 W32/Bdoor.MG!tr.bdr
F-Prot 4.3.2.48 06.01.2007 W32/SecRisk-ProcessPatcher-Sml-based!Maximus
F-Secure 6.70.13030.0 06.01.2007 Backdoor.Win32.Small.mg
Ikarus T3.1.1.8 06.02.2007 Backdoor.Win32.Small.mg
Kaspersky 4.0.2.24 06.02.2007 Backdoor.Win32.Small.mg
McAfee 5044 06.01.2007 BackDoor-DJJ.svr
Microsoft 1.2503 06.02.2007 no virus found
NOD32v2 2305 06.01.2007 Win32/Small.MG
Norman 5.80.02 06.01.2007 W32/Smalldoor.FVQ
Panda 9.0.0.4 06.02.2007 Malware Generic
Prevx1 V2 06.02.2007 no virus found
Sophos 4.18.0 06.01.2007 no virus found
Sunbelt 2.2.907.0 05.30.2007 Email-Worm.Win32.GOPworm.196
Symantec 10 06.02.2007 Backdoor.Trojan
TheHacker 6.1.6.128 05.31.2007 Backdoor/Small.mg
VBA32 3.12.0 06.01.2007 Backdoor.Win32.Small.mg
VirusBuster 4.3.23:9 06.02.2007 Backdoor.Small.DTD
Webwasher-Gateway 6.0.1 06.02.2007 Trojan.Hijack.Explor.273
We build the server with default option.

-RTelv backdoor: F1/P2

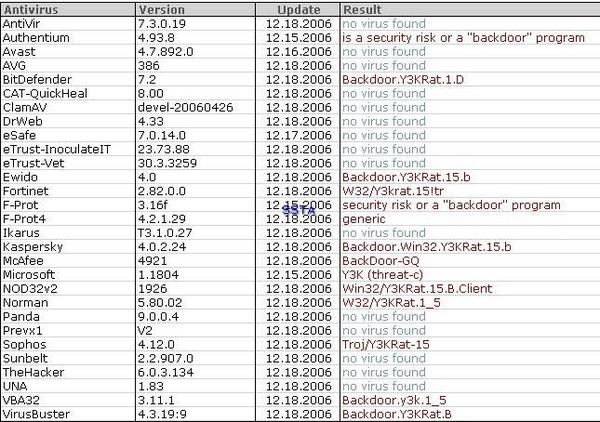
-Y3KRat: P1/P2
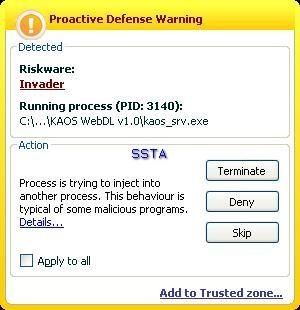
-KAOS Web downloader: P1/P2
-Ultimate Rat: P1/P2

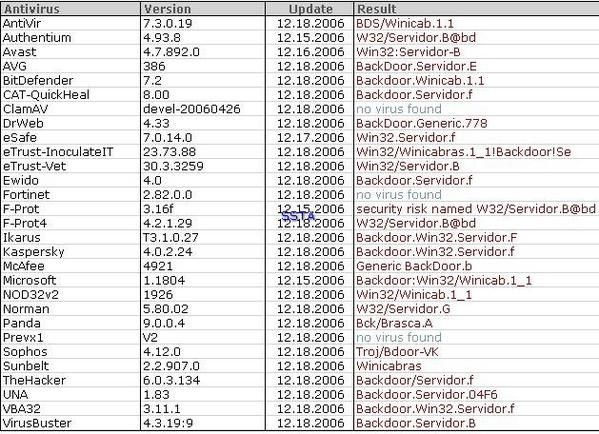
-Trojan Wincabras (backdoor Servidor.f): P1/P2

-Kaotan Trojan Downloader: P1/P2

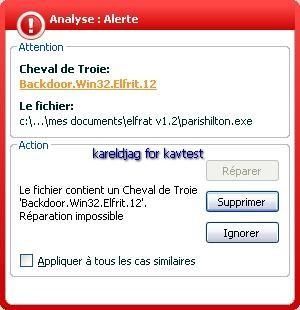
-ElfRat: P1/P2

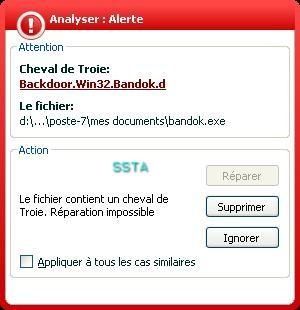
-Backdoor Bandok.d: P1/P2
-ExploitDoor.103: P1/P2


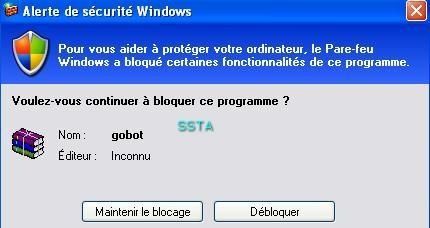
-Backdoor Gobot.u: F1/P2


-Generic IRCBot: P1/P2
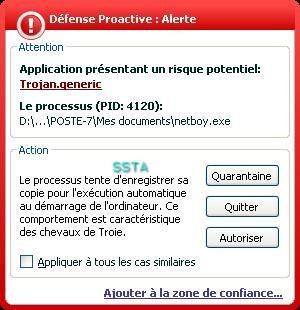
-Backdoor NetBoy.10: P1/P2

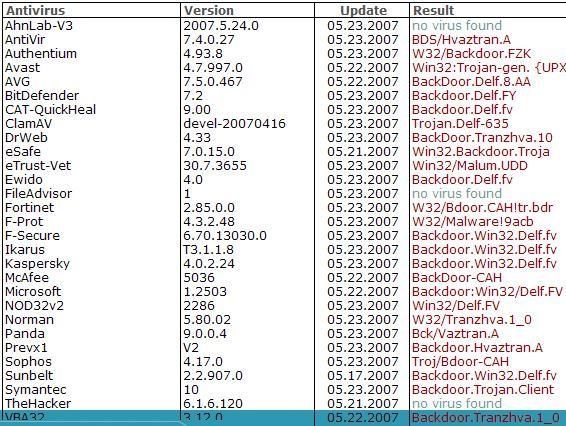
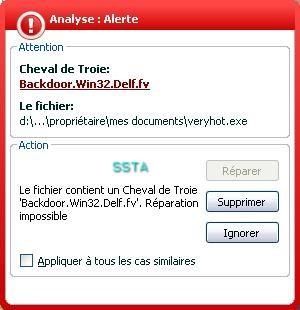
-Backdoor.delf.fv: P1/P2

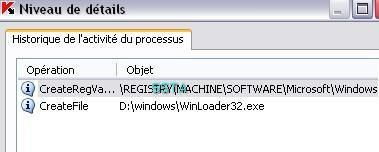
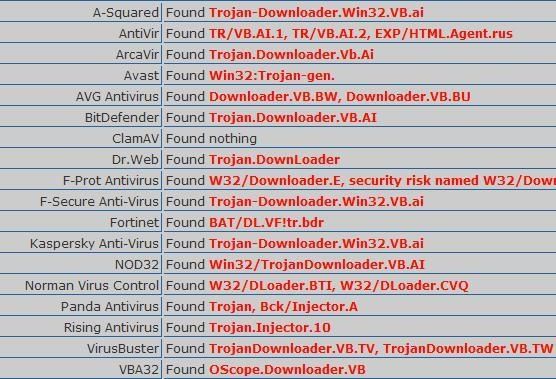
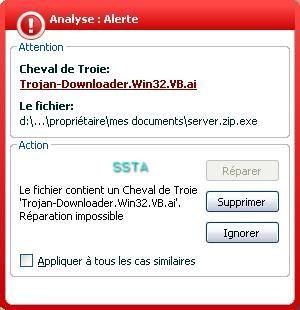
-Trojan Downloader Win32.VB.ai: P1/P2
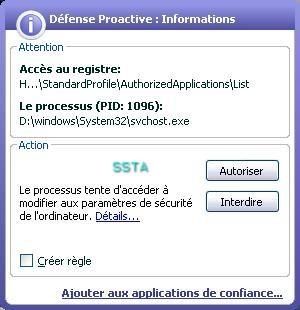
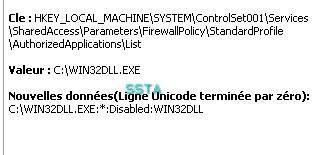
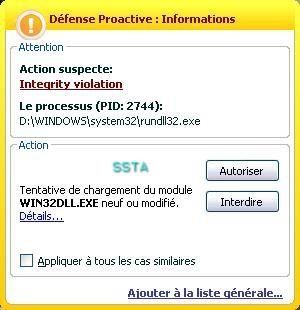

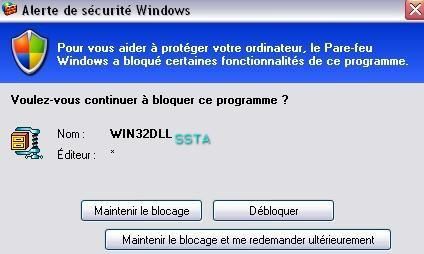
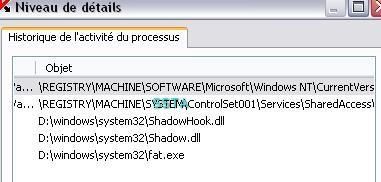
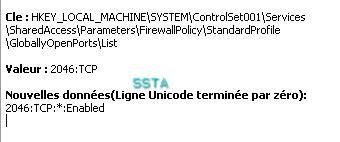
Windows firewall does its job too:
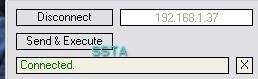
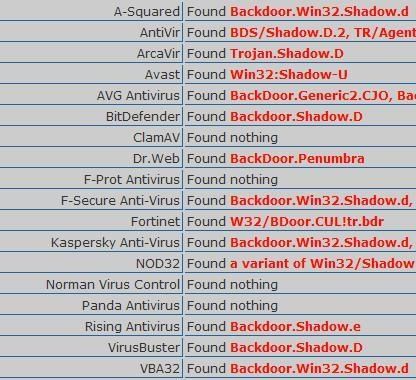
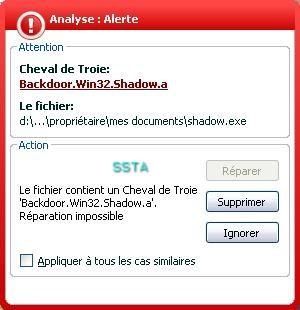
-Backdoor Penumbra/Shadow.a: P1/P2

-Backdoor Uhil.c: P1/P2

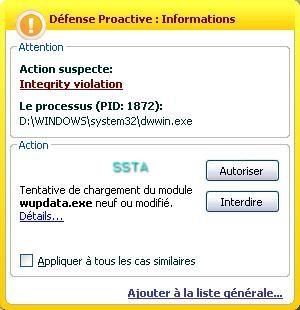

-Niwamp backdoor: P1/P2

This backdoor is interesting: it can be sent as a simple plugin to a target victim: the victim copy the dll in Winamp folder, and the attacker will get a remote command on 24501 port...
And as only a few antivirus detects it (see above), we can be sure that this backdoor was really used in the wild.
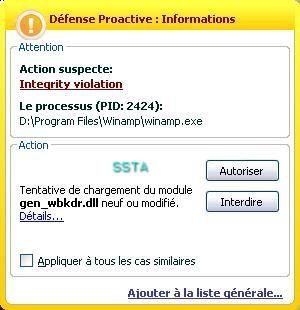
If we allow the dll (the effectiveness of HIPS is often user's knowledge dependent):

NEXT : Rootkit tests
