KAV TEST Part 1
FIRST PART based on the behaviour
NB: "Accès refusé" on screenshots means "Access denied".
1) Execution protection
a) with the TaskManager launched via Ctrl+Alt+Del: F1/F2
b) with srip32 launched by explorer.exe: F1/F2
c) with shellcode for running notepad.exe: F1/F2
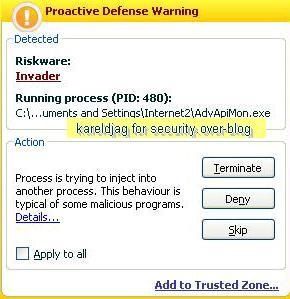
d) launching calc.exe via an other executable:
-with a specific tool: F1/F2
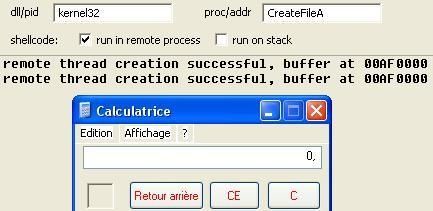
-with AdvApiMon: P1/P2
NB. It's important to note that the configuration by default does not act as an application firewall: for that purpose, it requires to add a list of applications to monitor like the browser for instance.
2) Self-protection
a) Process termination
-with the Task Manager: P1/P2
-with cmd (Task kill): P1/P2 (access denied)
-with APT (kernel method): P1/P2
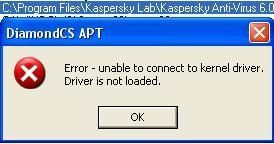
-with IceSword: F1/F2
NB: this is here not an issue: the driver kilf.sys (the base of kav protection) is still loaded and active in memory: the program is not fully terminated, disabled or deactivated.
That's why it's important to mitigate termination test results (AV/HIPS/Firewall).
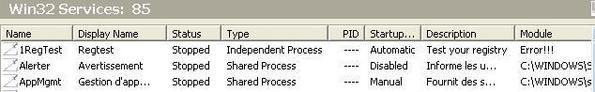
b) Service termination/deactivation
-with CMD (net stop): P1/P2
-with Osrloader: P1/P2
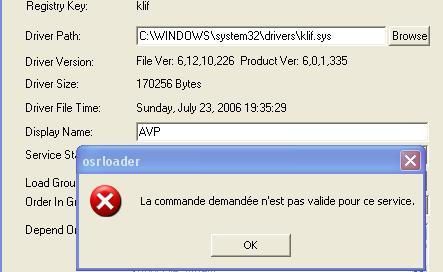
-with IceSword: F1/F2
c) Driver unloading
-with Drvloader (stop the driver): P1/P2
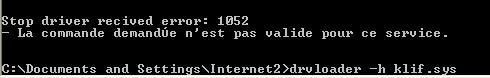
-with SDTRestore: P1/P2
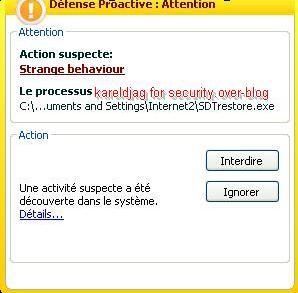
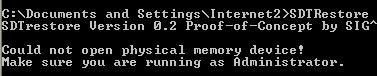
-with driverloader: P1/P2
d) Process and memory dumping
-with PmDump: P1/P2
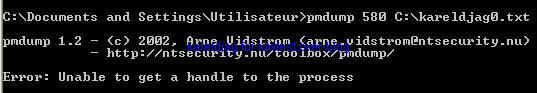
-with UH (memory editor): P1/P2
As we see we can't dump avp.exe:
2) Kernel protection
a) Crashing the computer
-with Bang: P1/P2
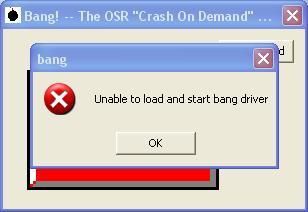
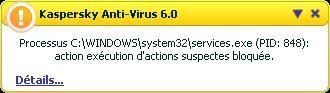
-with Regtest2: F1/F2
NB. the computer crashes but there is no confirmation at the reboot with the regtest dialog boxe (the service is blocked from running at the reboot).
-with a BSOD tool: F1/F2
-hooking Service.exe with Kapimon: P1/P2 (unable to load Kapimon's driver)
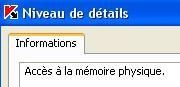
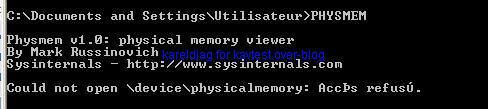
b) Physical memory access
-with Physmem: F1/F2
If we use Helios anti-rootkit HIPS for the same test, the access to physical memory is easily blocked:
-with SSDTRestore: P1/P2
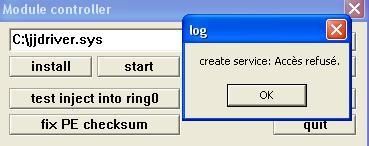
c) service/driver installation:
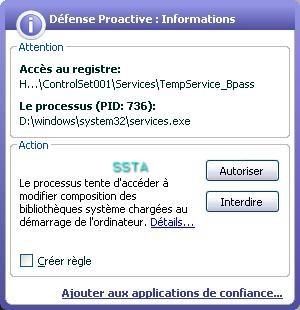
-with a "Ring 0 injector" : P1/P2
-with a kernel driver manager: P1/P2
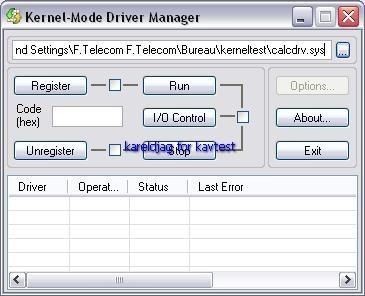
-register calcdrv: P1/P2
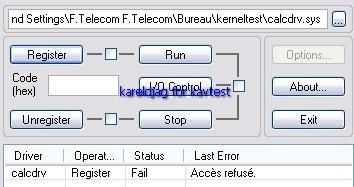
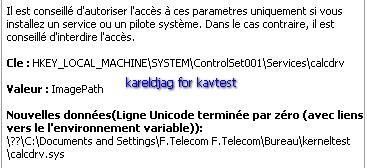
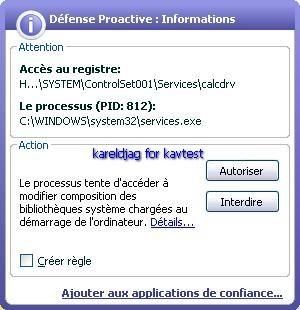
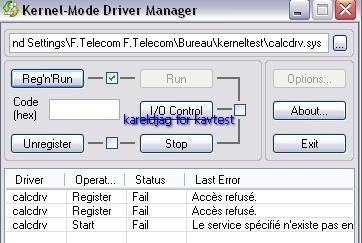
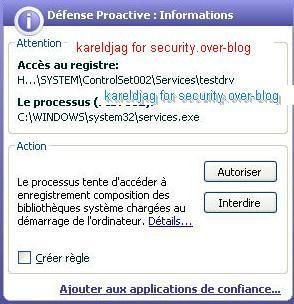
NB: here kav blocks only service/driver installation (register, or register and run option), but is not able to block the driver from loading once this one registred (requires an "allow " answer to the registry guard alert).
3) Integrity Protection
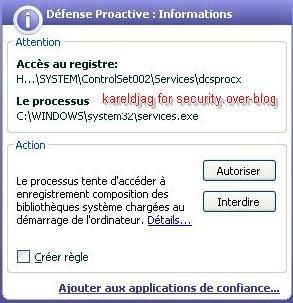
a) Integrate new dlls in System32 folder
-with BoWall: The new dlls are successfully added into System32 : F1/F2
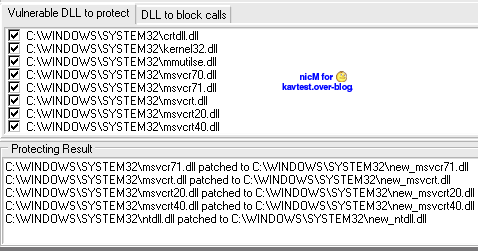
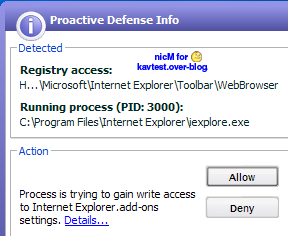
-with PrivBar : P1/P2
The toolbar is detected when it is activated in IE (after installation), and is disabled once the browser is restarted, if "Deny" was selected :
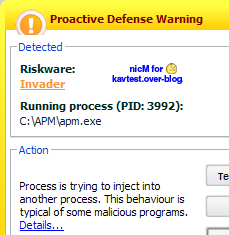
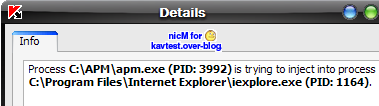
b) Load and unload a dll in Internet Explorer with APM
Kav detects both the dll loading and unloading : P1/P2
c) dll injection
-in IE with Copycat (leaktest): Code injection is blocked, then the "exploited" file can't be downloaded : P1/P2
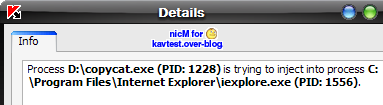
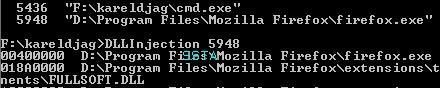
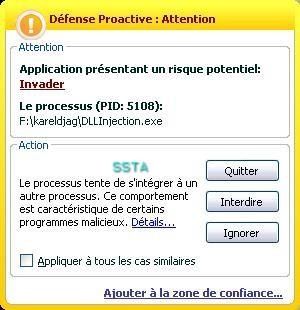
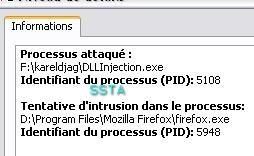
-in Firefox: P1/P2
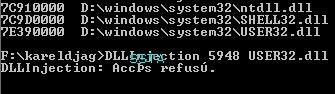
-in AVP.exe (service and Gui) and TCPview.exe with Zapass: P1/P2
-in explorer.exe (with a too specifically designed for that) : P1/P2
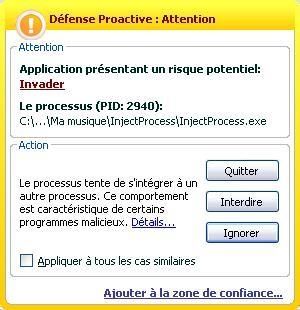
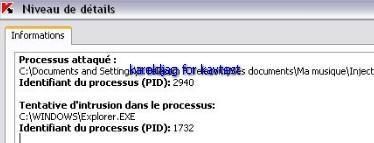
-injection in avp.exe with another tool: P1/P2
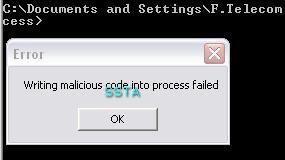
-Global Injection (in all running processes): P1/P2
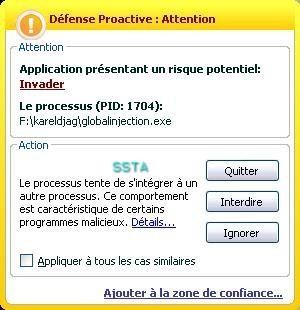
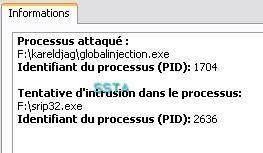
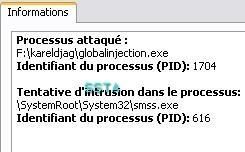
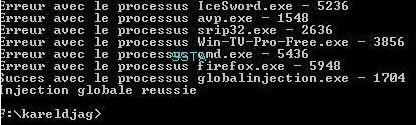
NB: this is here a masochistic tool: the global injection concerns all running processes, the tool itself included.
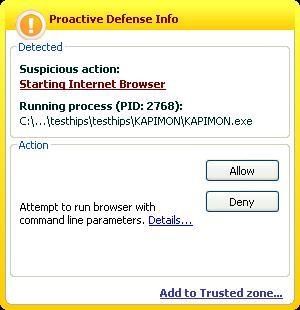
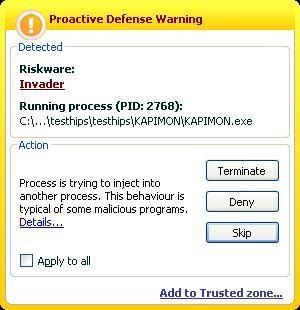
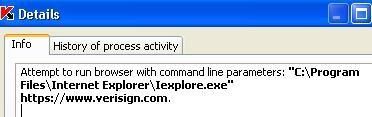
d) Hooking and hijacking IE with Kapimon: P1/P2
Here the test can't run since the Kapimon driver is blocked from loading.
If we allow it, we notice that KAV detects the browser hijacking:
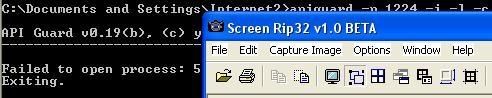
e) Process Modification via API with Apiguard (vs service.exe and avp.exe): P1/P2
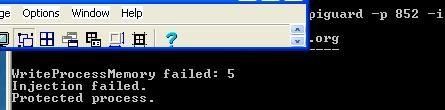
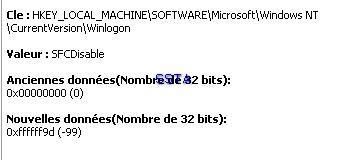
f) Windows File Protection deactivation: P1/P2
-tool 1

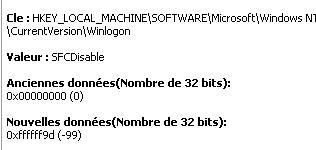
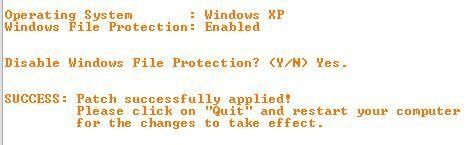
-tool 2:
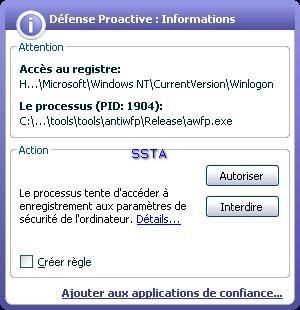
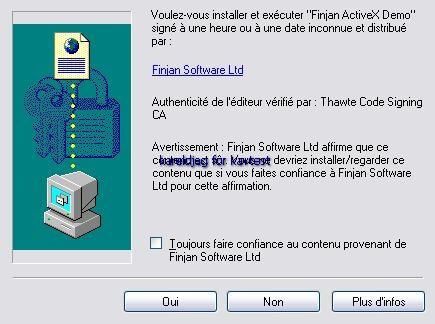
g) ActiveX installation (Finjan online tests): P1/P2
-With Internet Explorer: P1/P2
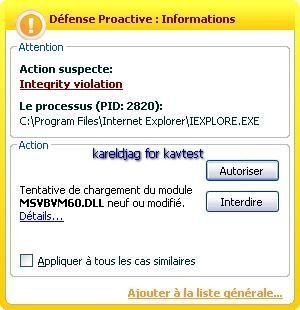
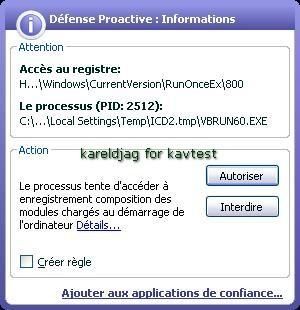
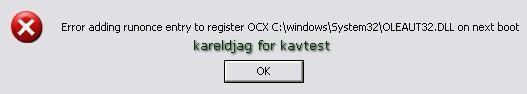
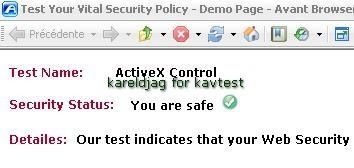
-With Crazy Browser (installed after KAV installation): F1/F2
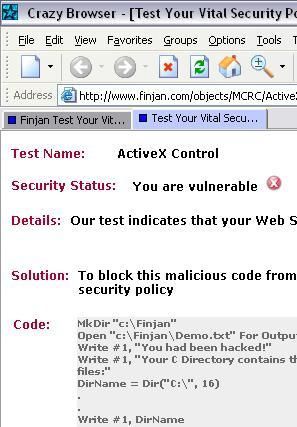
Here the log.txt file created on C:finjan folder:
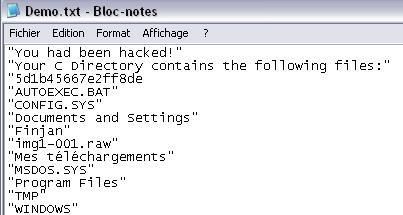
NB. Kav takes a finguerpring of already installed component only: it's neccesary to add each application in the configuration list (Integrity protection).
In addition, most browsers are able to protect their own integrity without third party programs (case of IE against ActiveX, via security options parameters).
h) Disable TaskManager: P1/P2
-with a RAT: this is here an option available in many RATs and trojans like this RAT used for this test (OM is just a name for the server):
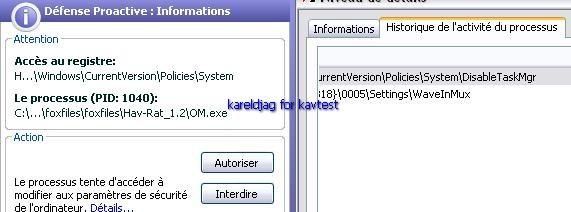
- with a hack tool: P1/P2
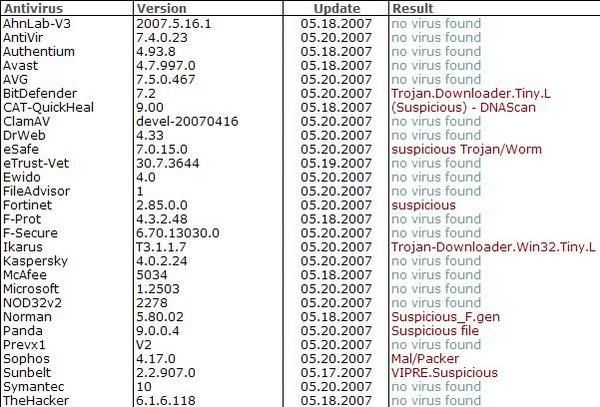
All scanner engines are sleeping, except for BitDefender:
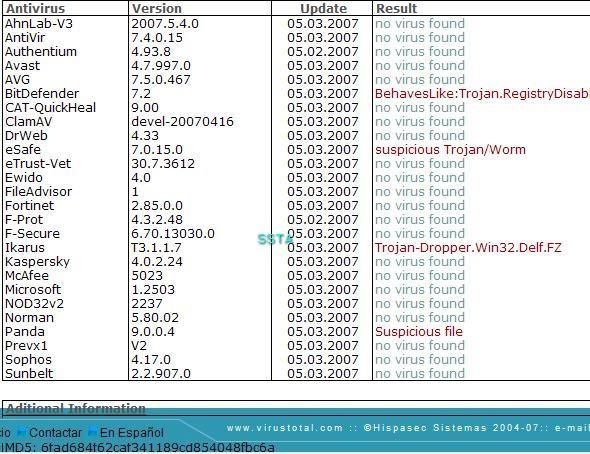
An online analysis is available here.
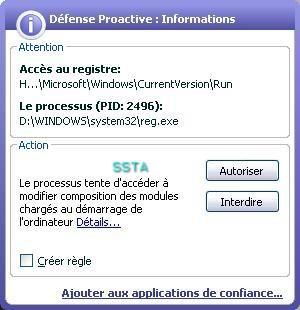
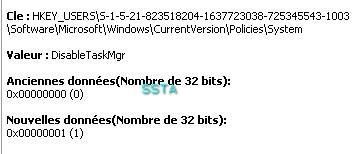
i) Bypassing File system permission: P1/P2
This tool uses system's privileges by installing itself as a service.
As often, heuristic engines like to play a funny quizz: suspicious, trojan/worm...