STEALTH KEYLOGGERS TEST
C) Stealth keyloggers:
Here only the detection is concerned : these commercial programs needs to be installed first with administrator privileges.
Some keyloggers hide their own folders (not seen in Program Files folder).

The result are often:
F1: fail result for the Proactive module: no "hidden object" alert of the hidden object (process mostly);
P2: The scan or the antivirus resident has detected "something suspicious" (a module, a driver etc) that warns the user.
Detection of the "keylogger behaviour": see kavtest2.
PDM: proactive module.
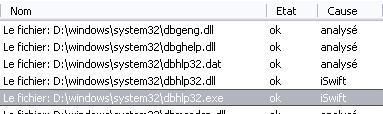
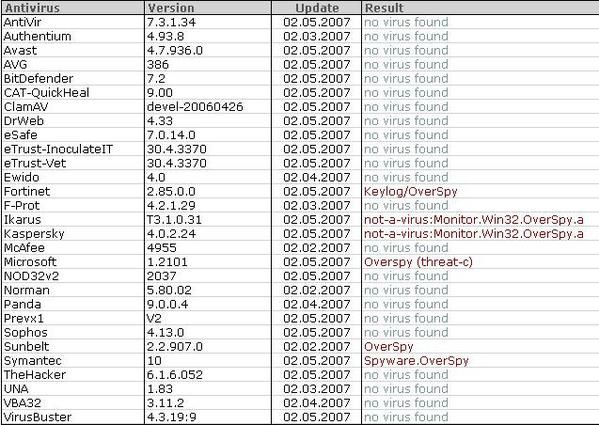
1) Overspy: F1/P2
Detection with IceSword, McAfee Rootkit Detective:

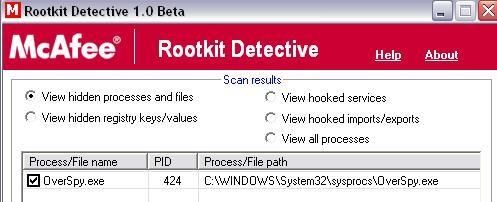


Kav does not detect the hidden process (F1), but as this commercial keylogger is integrated in its riskware database, the file antivirus reports the event (P2).
2) Beyond Keylogger: F1/F2
Kav does not detect the stealth keylogger (PDM or AV scan and resident).
For comparison, here's the detection with IceSword, Darkspy, Gmer, McAfee Rootkit Detective and Unhackme:
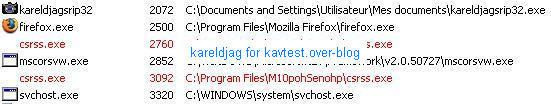
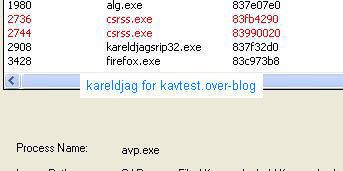
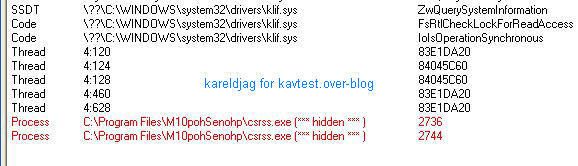

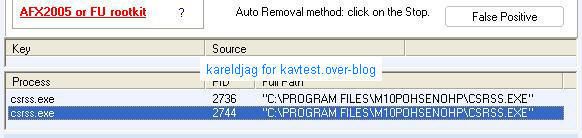
As usual Unhackme likes to play its stupid game (AFX2005 or FU rootkit?): we highly suggest to Dimitry and Greatis to take a look at this rootkit test and to update seriously their keylogger database (Elite is out of date now).
3) Family keylogger: F1/F2
Detection with IceSword:
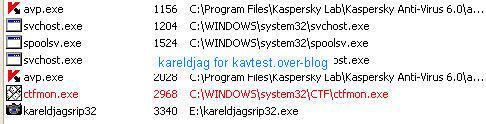
4) Advanced Invisible keylogger: F1/P2:
Here Kav does not detect the hidden process (F1).
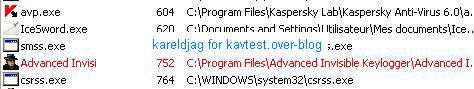

5) AceSpy: F1/P2
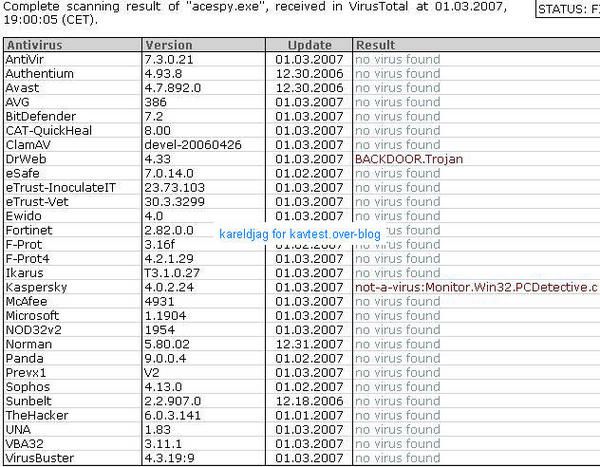
Kav is one the rare antivirus which integrates this keylogger on its database (P2).
Detection with IceSword and Gmer:
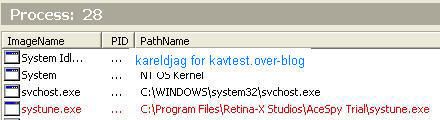

6) PC Inspector: F1/P2:
Detection with McAfee Rootkit Detective:

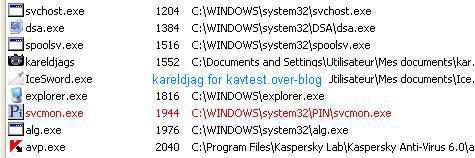
7) ActualSpy: F1/P2:
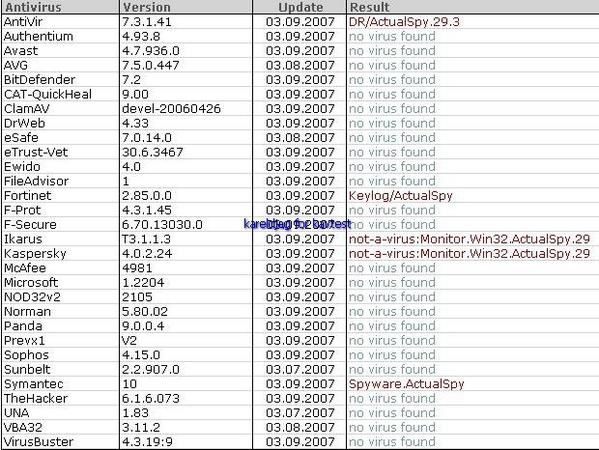
Detection (hidden process) with IceSword, RKU and SecurityTaskManager:
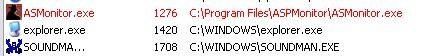
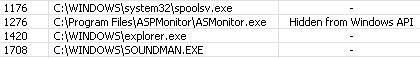
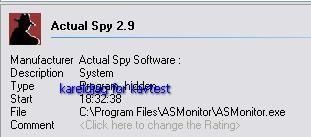
The scan of critical objects (fast) gives no result of infection: the stealth keylogger's objects are seen but not reported as hidden and malicious (even if Kav has a pattern file for this keylogger):
8) Powered Keylogger: F1/P2
This is one of the most interesting example of stealth keyloggers.
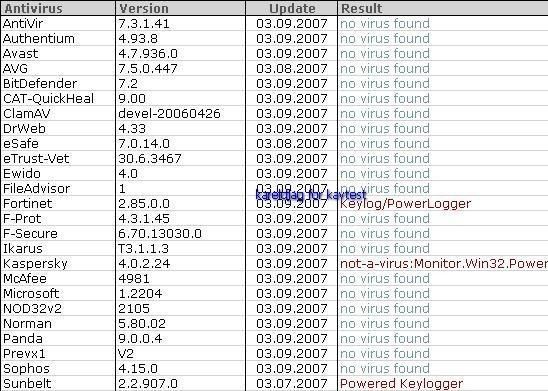
Detection of hidden objects with some detectors:
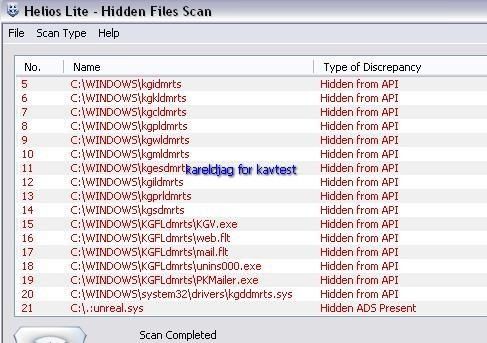
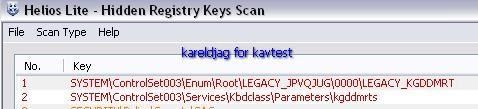


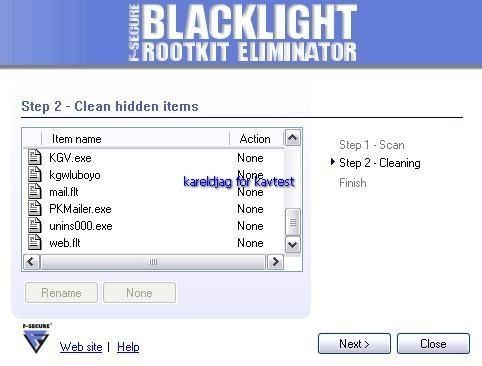
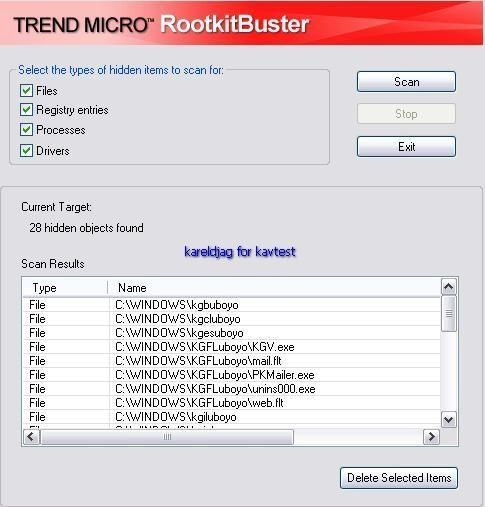

R.Revealer:
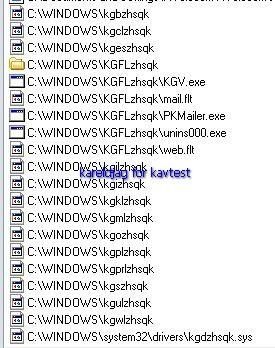
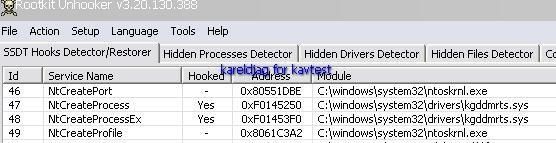
But RKU like some other Task detectors does not display the driver as hidden ("from Windows API"):

9) Wiretap Pro: F1/P2:

Like most stealth keyloggers, the hidden method is here basic and the process is even detected by Process Explorer (but not by Task Manager clones!):
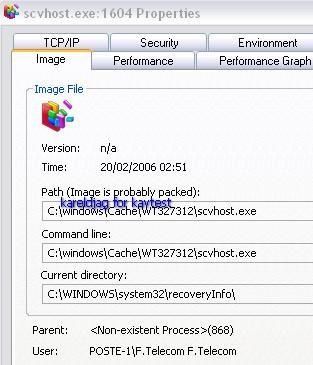
Like some other rootkits (MsSync) or stealth keyloggers, the hidden process takes advantage of terminology of system's processes (here svchost.exe/scvhost.exe related to many system services and familiar for most users).
Detection by RKU, SysCheck, IceSword and McAfee RKDetective:
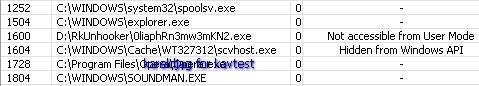
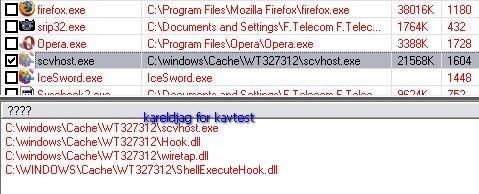
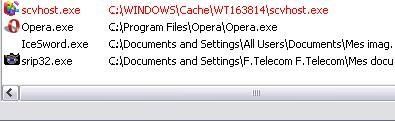
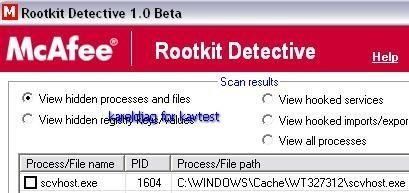
In this case again Kaspersky proactive module does not detect the hidden object (F1), and a fast scan (critical sector) can't be considered as very reliable:
The hidden process is not displayed as hidden, neither detected as malicious:

Some module are detected as OverSpy Monitor/Keylogger:

And other ones as Wiretap:


10) Elite Keylogger: F1/P2

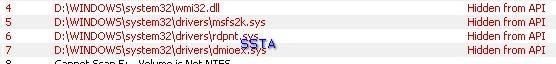

11) Metakodix Keylogger: F1/F2

Detection with McAfee Rootkit Detective, DarkSpy, RKU, Panda, HeliosLite and System Repair Engineer:
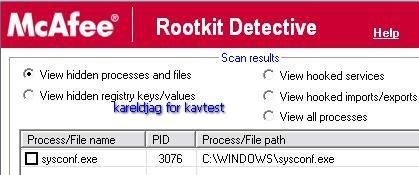




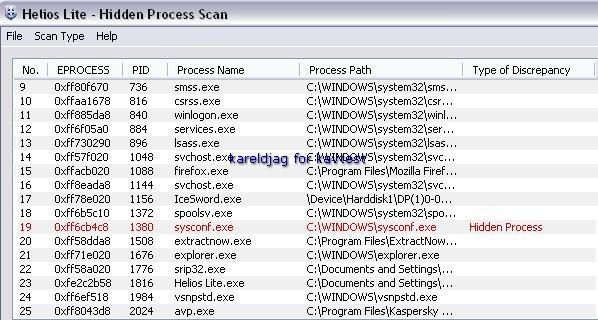
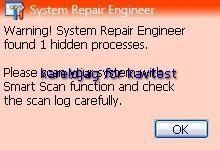

Even with a quick scan of critical object, Kav does not detect that a stealth keylogger is running:
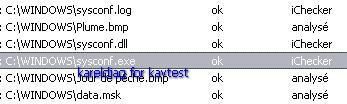
An example of log:
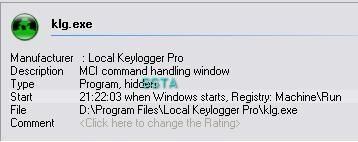
12) Local Keylogger Pro: F1/F2
This keylogguer os not known from Kav:
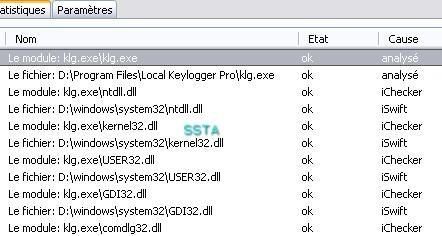
Local keylogger hides from the Task Manager but not from task tools:
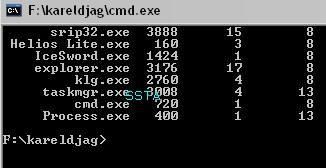
klg.exe is not displayed as hidden by rootkit detectors:
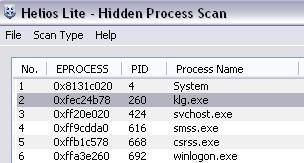
If we run Security Task Manager, there's an indication that the process is hidden:


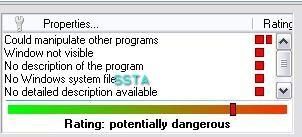
13) Mini keylogger: F1/F2

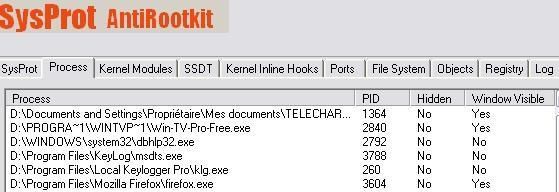
In this case again most detectors does not display the process as hidden (it is hidden from the task manager).
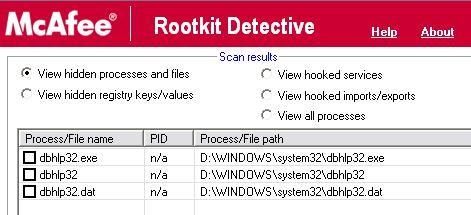
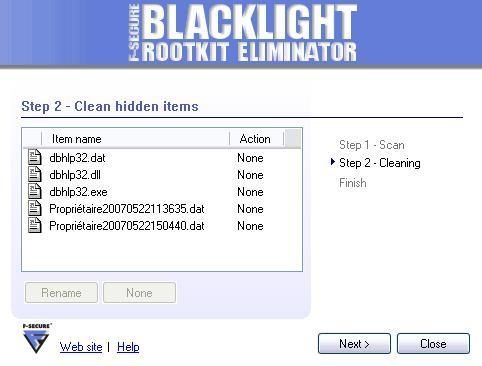
Some scanner detectors like McAfee Rootkit detective and F-Secure BlackLight and even Process Monitor (bu not Process Explorer) detect the hidden objects:

For Kaspersky, all is OK:
Startup registry scan:

Critical sectors scan (running appalications, Windows folder etc): all is OK: