ENDPOINT AND DATA THEFT TEST
These tests concerns endpoint threats: with the success of USB key, IPOd, and removable media, this is an excellent attack and infection vector.
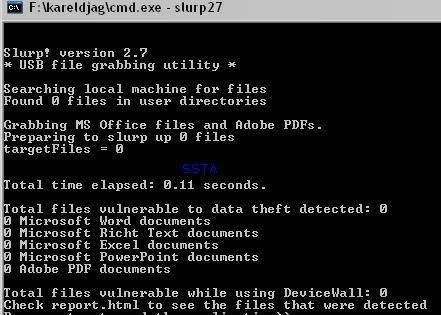
Tests a, b, and c are simple demo which dump the content of My Documents folders, and file type content (Slurp).
Other test can really be a threat, locally (any computer with a physical access) or remotely (social engineering1 attack via MSN messenger and the shared folder for instance).
We have also added classical tests related to sniffing, data theft vis trojan and remote administration tool.
With the number of connected devices and the success of USB 2.0, a new class of security threats and products have emerged: here for sharing USB key, here for remote access, here for monitoring children etc...
Therefore there's a real Endpoint security business in general, and USB security business in particular.
If some specialized and sophisticated products can be necessary in a corporate environment, this is not the case in a home environment: some editors sell softwares for 40 dollars/Euros when these softwares just provides simple policy restrictions that can be replaced by a simple reg file...
It's also important to note that endpoint threats is an interesting idea to bypass protection provided by virtualization and "reboot and restore" softwares: these protection take only into consideration local and preconfigured hard drives, not removable drives like USB key for instance: it's not difficult to build an autorun and portable USB rootkit which loads each time the USB is connected...
But VMWare already takes care of that (more info here).
Here we only explore Endpoint threats with data theft and malwares infections.
A good summarize of these threats can be found on this pdf.
For more information about attacks against USB hardware devices, we suggest to take a look at these two pdf (same authors):
-USB hardware tokens:
-The same paper at BlackHat
1. Social engineering: the Melani institut has released a report which relates the increase in Social engineering attacks.
1) Demonstration tools
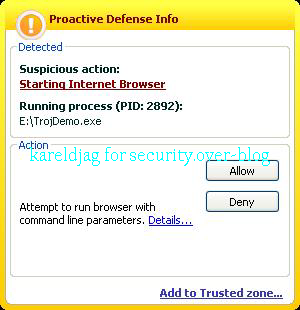
a) Trojan Demo: F1/F2
Kav does not detect that files are listed and copied, but only IE hijacking (required for the results of the test).
b) Finjan JPG: F1/F2
We click on the jpg and My Documents files are copied on a folder created on the desktop and called "You have been hacked!"
c) USB Slurping: F1/F2
2) Endpoint threats (USB/CD Rom/IPod dumping and malwares)
a) Dumping the full content of a USB key without user's awareness: F1/F2
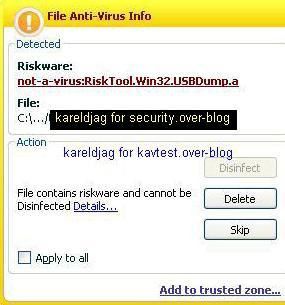
We use a tool designed by a french searcher that we call Spy USB (not its original name, but the classification of BitDefender).
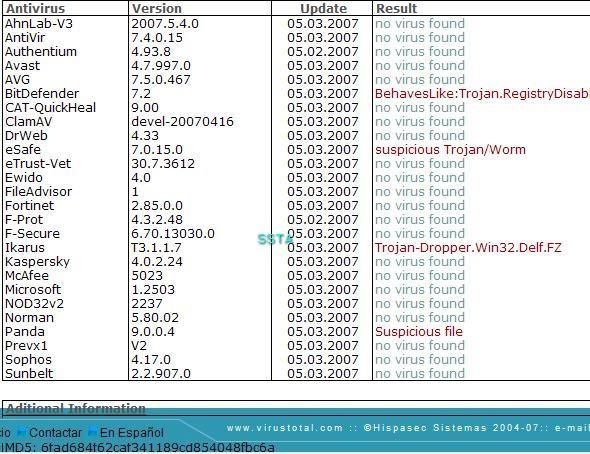
This enhanced version is not detected by maost AV scanners:
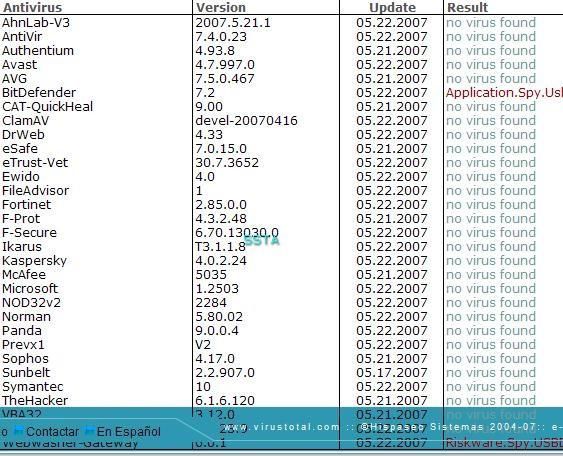
Kaspersky antivirus is well known to have one of the most reliable database, but in our case, it detects nothing:
"Don't worry gentle users: all is ok..."/ "Dormez les petits, tout va bien"/ "Schlafen Sie die Kinder, alles ist ok!"/ "no preocuparte a niños, todo es aceptable"...
This threat is not new: check this article, and especially the pdf paper from SPI Dynamics ("Plug andd root: the usb key of the kingdom").
We do not give its original name for ethical reasons: it would be very interesting for ill-intentioned persons to add this file on start up on any public computer, and to come back from time to time in order to take a look at the content of dumped USB keys and CD Rom.
USB can also be used to distribute malwares (example here and here).
Or it can be used by an ill-intentioned employee (computer espionage) on any computer that he can have access...
In this example we use a USB key where are stored files and folders.
We run the dumper and connect the USB key.
As it is shown by the next image, the content of the USB device is copied to the hard drive (in "USB Spy" folder"):
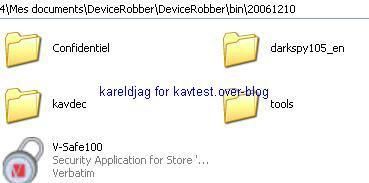
Only the files stored in the safe zone (V-Safe100 protected by a password) can't be copied on the hard drive: another reason to encrypt USB key (free tools are designed for that purpose).
As it shown above, the "confidentiel" folder is clearly copied from the USB key to the hard drive: it could be a bank listing or any important data and documents.
b) Dumping and copying specific and desired files from hard drive to Usb key (Thumbsucking) and vice versa
The new version of this USB utility can copy files from C: to USB key with an autorun file, play with Macro (word and excel), and dump the content of a USB key with extensions filters (only zip. or .jpg files for instance).
Now we'll copy a file located on the hard drive directly on the USB key: the file is stored with an autorun configuration: each time the user connects the USB key, the file will be executed automatically.
This file could be:
- a script,
- a backdoor,
- a shell execute which launch IE (Internet Explorer) to specific URL that was designed to install a rootkit for instance (these pages really exist in the wild),
etc....
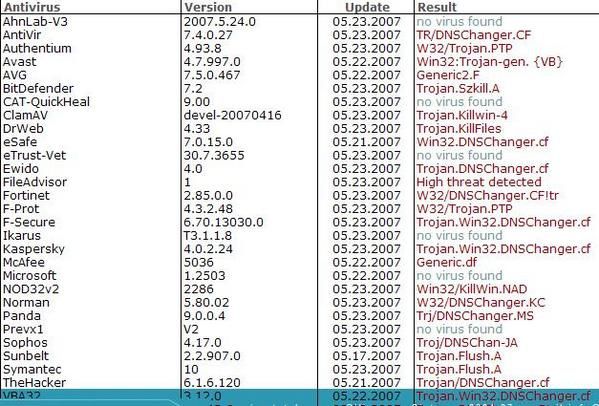
-Example 1: F1/P2
Result of Virus Total Scan:

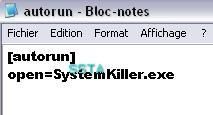
-example 2: F1/F2
Here we'll show that it's not difficult to use which malware we wants, even detected by the antivirus (black list).
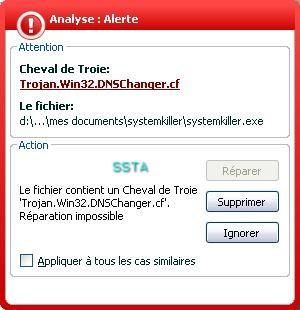
We take the trojan downloader Banload.agp that we rename as "smss":

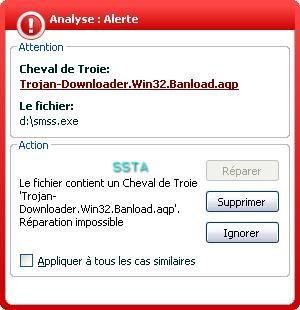
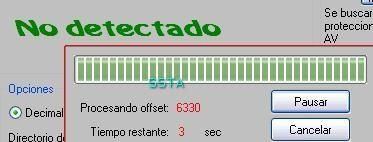
The goal here is to bypass the av scanner engine and the av resident by "playing" with the offset: no need run time packers (often a Russian roulette game) or malware reverse engineering (requires time and the "dear Olly" ).
Once our job done, we create an undetected copy of the trojan downloader:
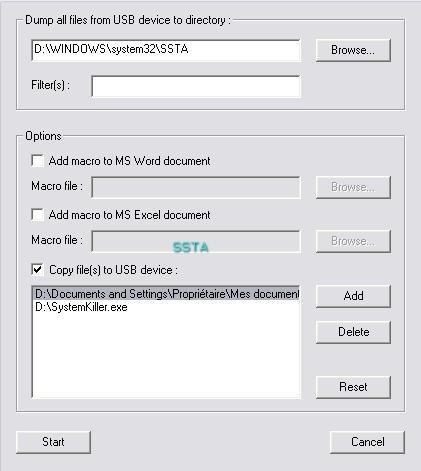
Now we can copy our undetected malware with an autorun from D to USB key, and filter the dump of the USB key for .xml files only:
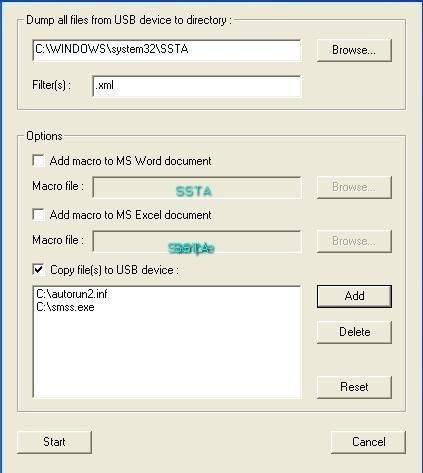
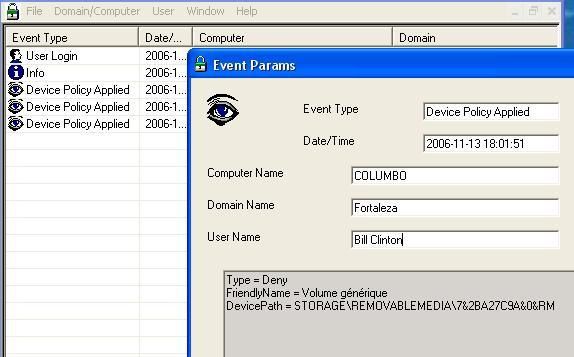
The content of SSTA folder before the test (empty):
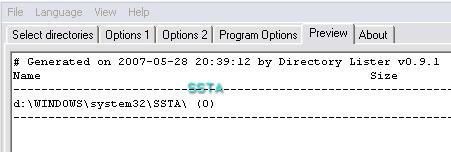
We have created a database of the USB files and Windows folder content before the test. By this way, we'll see:
- if the files (undetected malware and the autorun ) are detected as new or created on the USB key,
- if the desired (filtered) type of file is detected as new or present in SSTA folder.
We click on start (Kav has no reaction), disconnect and reconnect the USB key, and update the database:
And we check for created files on F: (USB key)
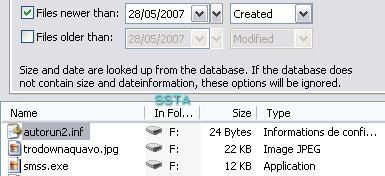
As it is shown above, smss.exe and the autorun file have been copied silently from D: to F:
Confirmation on the USB:

And the .xml file is copied from the USB key to SSTA folder (hard drive):

And it can be any file (bank listing, important data etc): it makes the protection of data very important, especially when we consider recent various incidents related to data leak and lost via removable drives and laptops.
We disconnect the USB and reconnect it again: the trojan downloader is executed automatically without any reaction from Kav...
Here again we show how it is easy to bypass the black list protection, and we can do this with any malware used for the methodology: who talks about 100% detection rate certified antivirus?
-example 3: F1/F2
In this example we use a simple trojan which gives a shell once executed.
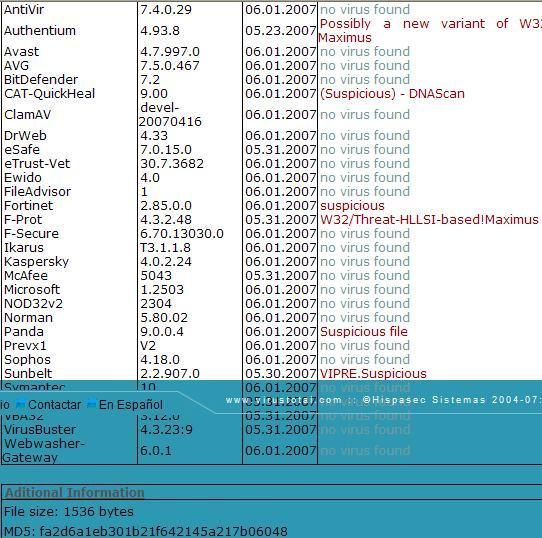
This recent trojan (may) is not detected by antivirus softwares.
We call it ShellTrojan.
We don't know who is Maximus, but it seems to be a VIP (a Very Important Parasite)...
This "pure backdoor" tries to bypass the firewall:
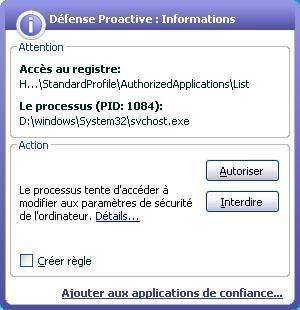
But in our case the full protection has not blocked the file from providing a remote command:
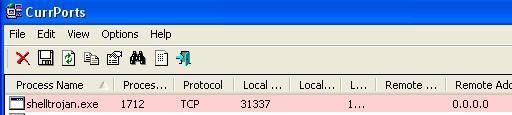
Now the ill-intentioned person can have access to the machine from any computer...perhaps via laptop, in a car, at 50 meters from the target host (Wardriving)...
c) Data loss: F1/F2
We use killwin (that we've already used in the first part as a registry disabler) which has interesting destructive function: it replaces the content of any text file (.txt and .rtf etc) by a sentence.
With notepad, we create a text file called "football":
Text file properties:
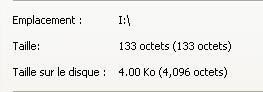
The "football" text file after the autorun of killwin:
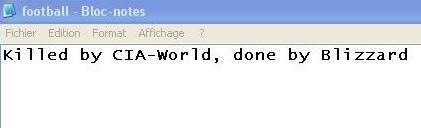
The size has changed (39 octets):
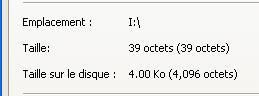
And it is the same for all text file stored on the USB (as we need them for test result compilation, they have been archived as .zip file before the test).
Example with a word file:
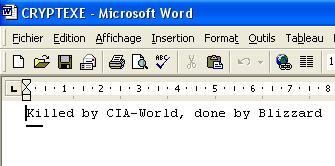
By by text files...or perhaps not: there is classical and forensic recovery softwares (an example of simple and free one here for instance).
This hack tool disables the registry, hijack the browser (IE as often), but delete the content of text files and makes non functional any executable.
The goal here is to focus in the endpoint threat: there's a lot of malwares designed to delete hard disk files, and why not USB content as it was the case for floppy in the past).
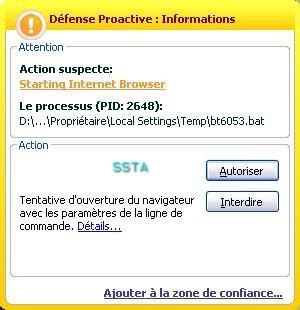
NB. There's many free tools designed for CD Rom or USB AUTORUN (like this one for instance).
NB. It's important to remember that this could really be an important security issue for an intrusion as it was reported by Bruce Schneier and this Darkreading article.
But this is here "making noise for nothing"...or perhaps "making noise for selling more and more security sofwares".
If we consider that System's hardening is the first step in the security process, then this USB insecurity threat should be prevented (disable autorun, write protect USB key etc).
An effective intrusion is stealth and fast, and leaving no trace is not absolutely necessary (traces is like no traces if they can' be exploited).
In the example, an ill-intentioned person leaves an USB key in a corporate environment.
The intrusion can be a success as it was shown by some of our examples.
But there's no really perfect intrusion done with physical access.
It's not difficult to prevent any digital fingerprint on the usb key...but what about the camera, what about the "human presence trace" (hair, piece of skins, odour).
Most of all, once the key connected and the System hacked, it means firstly that the IT Manager/System administrator is very incautious (non hardened system). But that's only the beginning of the forensic investigation: it's important to note that Windows remembers your connection:
Here with simple tools we can display all the connected devices:
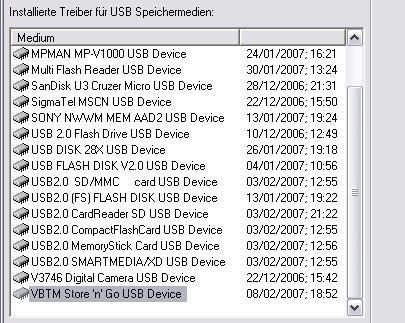
The latest USB name displayed is ours: anyone can audit his system with USBDeview, a free tool from Nirsoft:
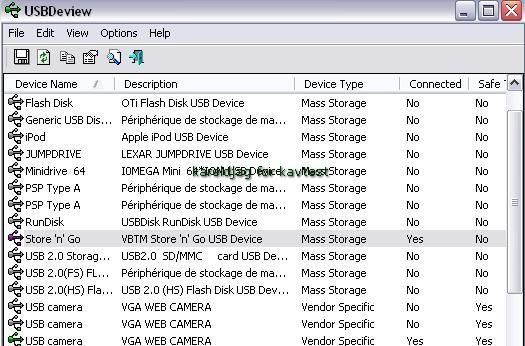
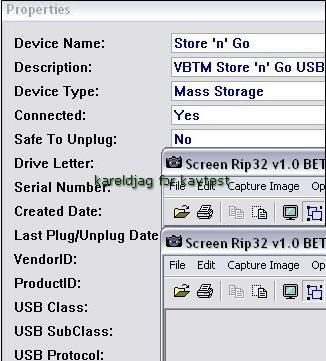
There's also some programs designed for professionals for a more exhaustive audit:
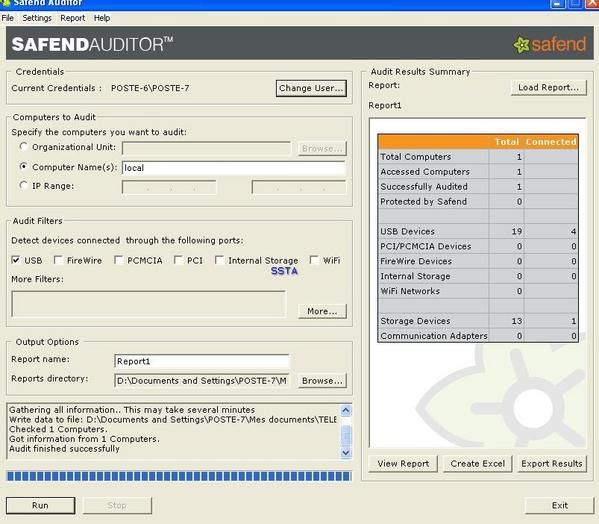
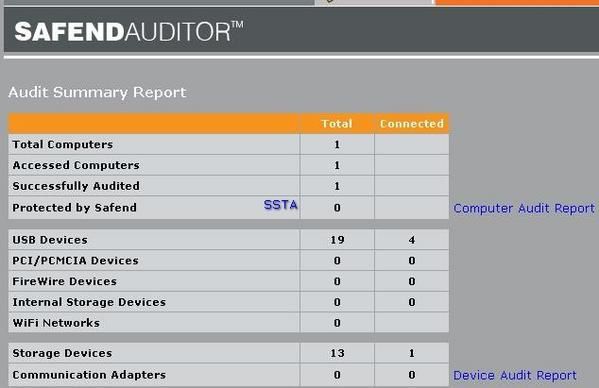
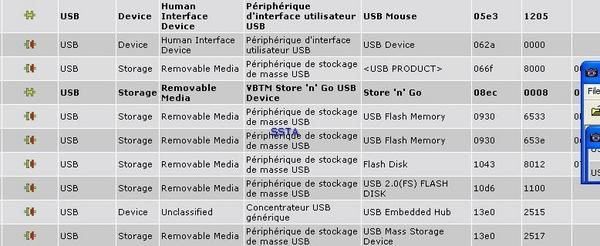
By this way, it's not difficult to obtain full details about the key (serial number, vendor ID etc) and to begin the investigation (where the key has been bought and by who if the payment was done with a check or credit card).
NB. It is not difficult to prevent this threat if the host is deeply hardened.
For users who wish simple tools, there is free protections available to deny access to external drives, and some HIPS (Viguard and Abtrusion Protector) takes care of this since a long time), as like as this recent one (we guess that this test will give some interesting litterature to the team...).
Here the device connected to the local host USB is represented by E):

If we apply restrictions:
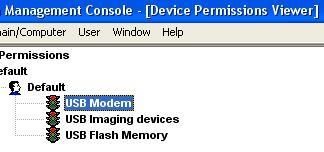
And the drive E is not displayed anymore by Windows:

d) IPOD Dumping: F1/P2
In this scenario we suppose that an attacker has a shell to a target machine, and wish to steal confidential data stored in a IPOD for instance.
He uses SMS Spoofing by choosing a trusted mobile phone number (the Boss or any trusted and influent person).
SMS Spoofing does not require specific know-how, and can be used by a kid of 12 years old: if some site (sorry, "registration disabled", this is a test, not a hacking tutorial :) ) and firmS are specilaized in this kind of service (more vicious is "spoofcards" for instance), this attack can be done via a simple browser...
As this attack can be done in real life for crime (also here) we highly suggest to vulnerable persons (children, teens, seniors etc) to never trust this communication vector:
And we recommend to use SMS and voice call back confirmation, and SMS signature for trusted sources (for example the mother can add his nickname at the end of each SMS etc).
Fortunately, technical solutions and countearmesures are available like Nc Mobile Token for instance.
NB. With the success of IPod, many products (hardware and sofwares) had been released: a free IPod dumper here for instance.
e) CDRom autorun:
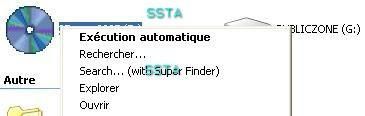
This test is a variant of the last one, but here we use another scenario with a social engineering attack by sending an advertising CDRom to a target user/company (CDRom content could be a limited version of pay management software for instance, or a "fake" porn DVD for users :) ).
-example 1: the autorun is configured to run a crash tool (crash the computer instantaneously): F1/F2

-example 2: destructive virus designed to remove hard drive files: F1/F2
-example 3: a pure backdoor: F1/F2
-example 4: launch the browser to a specific URL: P1/P2
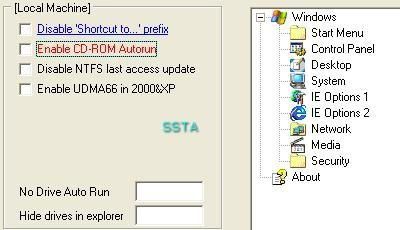
To prevent this kind of possible threat, it's highly suited to disable the autorun or USB and CDRom.
Here's what happens when a USB key or a CDRom is inserted with the autorun enebaled:
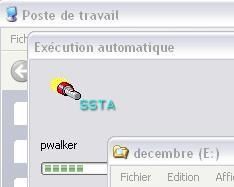
The restriction can be done easily by using Windows (example here and here):
Example with the CDRom autorun (all removable drive option is better for a high level of restrictions):
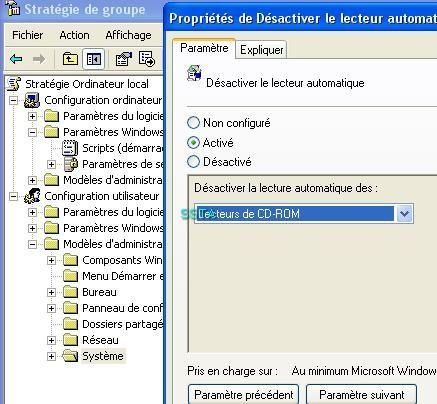
For beginners and normal users who are not familiar with the registry, the can use RegTickPro, a free tool which include hardening feature .
f) Stealing onling bank ID logins: F1/F2 for detection (and P1/P2 for prevention)
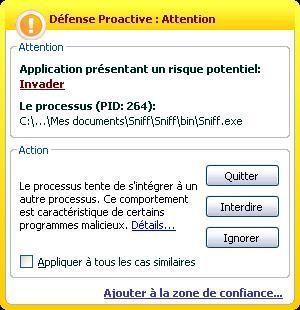
Here only the detection should be considered (this is not the victim who launch the executable which generates an invader alert).
Security risks when using public computers is not new (article here or here).
In this test we suppose a classical scnario which can occurs for any public computer users.
In our scenario we suppose that a traveller or a tourist needs to take a look at his bank account.
As there's no affiliate bank on the country he's visiting, he decids to go on a public computer (internet café).
Unfortunately, an ill-intentioned person has put a trap to capture confidential and financial informataions and data.
This trap can be any keylogger (stealt and hardware), but in our case we choose a video capture tool which is an excellent way to bypass virtual keyboard authentication provided by online banks.
We suppose that the internet cafe manager has restricted access to tha the hard drive (C:).
Therefore our "bad guy" (sorry, computers crimes statistics shows that there's more "bad guys" than "bad girls" ) uses a portable version of video capture tool (CamStudio Portable) that he launch from an USB key.
As he has no access to the hard drive, he chooses to save automatically the .avi file on the USB key.
It's easy nowadays to find small USB with high storage capacity: this is for instance the case of Sony micro vault tiny.
And our 'bad guy" hides its USB key with camouflages (black color key, hidden with cables): as the key is connected in the reverse side of the computer, there's no way for the public computer user to detect it.
The only limitation concerns the size of the .avi files, even with compression: about 10 Mo every minutes...
As this application is not recennsed as malicious by antivirus, the last problem is to hide the Cam Studio icon on the systray.
The test was done under real condition (Internet cafe, with the authorisation).
As french testers we have chosen a french bank (BNP Paribas): in this case, the account number and the number code are necessary.
Naturally, all the data shwon in this video are fake data, that's why the authentication does not work.
The video can be seen in the french youtube here.
But the quality of the video is quite poor, so we sugges to download the full video at Rapdishare, and to use tyhe full screen option of your best palyer (we recommend The KMPLayer).
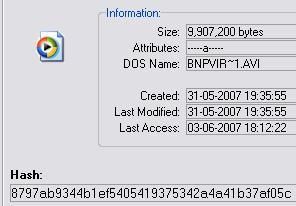
A few info about the .avi file (SHA1 value):
The video on Dailymotion:
http://www.dailymotion.com/kareldjag/video/x24h5l_bnpvirtualkeyboardowned
Direct link here.
NB. The video has been censored by an Idiot: our logo SSTA was censored, but does this idiot knows what it means?
The problem is that this Youtube clone stores illegal content (video, films and music without copright) that is not censored.
Another paradox of the web business...
The file as .rar archive at Rapidshare:
A few info about the file SHA1 value):
http://rapidshare.com/files/34679518/BNPVirtualKeyboardOwned.rar (direct download here).
3) Spying and stealing data via sniffers and malwares
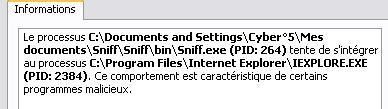
a) Stealing data via an HTTP RAT: F1/P2 (the RAT is known from Kav database).
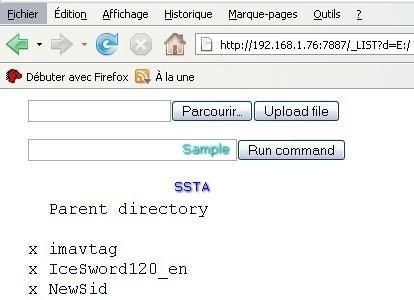
With only the PDM enabled, this HTTP RAT open 7887 port, and we can establish a remote connection via the browser, and have access to all desktop and external drives:
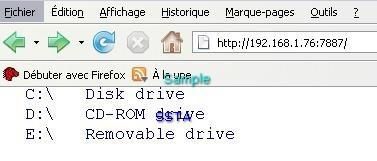
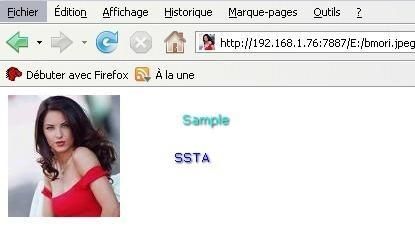
We can browse to all drives and upload any file, a simple .jpg of Barbara Mori in our example, but it can be any confidential file (private photos, bank listing etc).
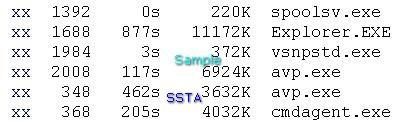
What's running:
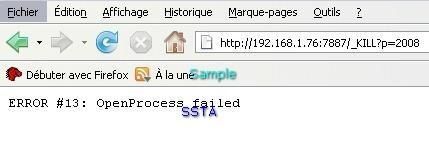
If we try to terminate the antivirus (avp.exe):
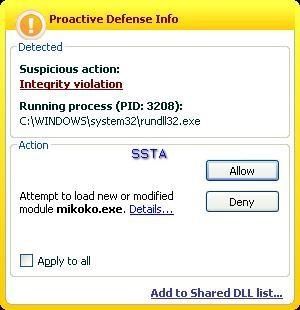
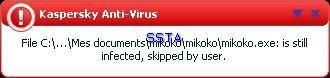
We have access to the desktop and all connected devices.
b) Wintro trojan: F1/P2
This trojan is very simple to use and very effective: the attacker just needs to send the server file to the victim, and to know his IP: then he'll get a share to C:
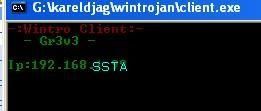
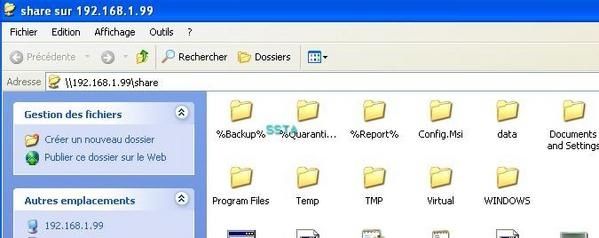
c) CMD Sniffer: F1/F2
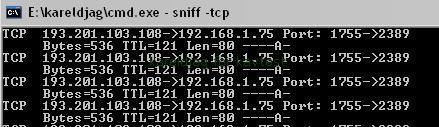
d) Sniffer with a gui: F1/F2
-example 1

-example 2
e) HTTPS sniffing of IE: P1/P2
This tool is designed to capture "gold" data (ID bank account etc) during HTTPS connections.
f) NgSniff
-basic: we just run the sniffer from the command line: F1/P2
-advanced mode: by using Alternate Data Streams: F1/P2
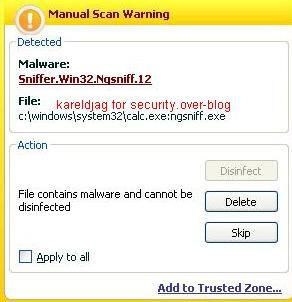
-remote sniffing (from host A to Host B): F1/F2
The sniffer is known from Kav database, but the packet capture is not done locally.
There's no perfect solutions against sniffing, we can mention Promiscan for instance (free version available).
g) Instant messaging sniffing: F1/F2
This test is done with a simple executable tool (no install).
A capture during a yahoo conversation:
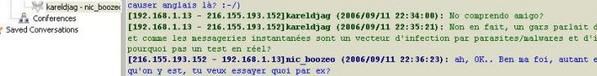
This AIMSniffer clone is not known from Kav database (F2 result).
NB: most of these tests are easily prevented by hardening Windows (System file permissions, using Regedit etc).
In order to prevent external drive content (USB key, IPod etc) from being copied, it requires just a registry tweak (write protect a key: more detail with this pdf).
Many softs free and paid can be found here about external drives protection.
But it's not necessary to open the wallet for : simple reg file, a turn in the BIOS or in the peripheral manager is enough in most cases.
For normal users who does not know how to disable access to CDRom or USB key, we suggest disabler tools from IntelliAdmin (USB/CDRom/Floppy Drive Disabler): they're free and very simple to use.
h) USB capture: F1/F2
Here we suppose a physical access and administrator rights.
This is not areal threat, and this test is done just for information purpose about spying possibilities.
-tool 1: F1/F2
-tool 2: F1/F2
4) USB Malwares:
For those who are not convinced, a few articles here, here and there and there.
a) with Worm Cekar/Delf.bg: F1/P2
Here we use a recent example of "USB malware" which has the ability to spy and steal intant messenging passwords (we do not use this chinese IM, so this test can be considered as an illustration of "USB malwares").
A description of this worm by McAfee here.
P2:
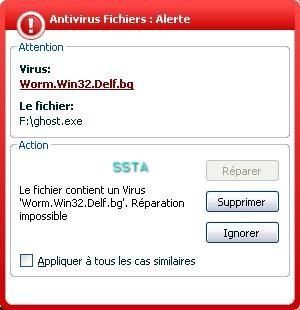
In a first phase, we have previously infected our USB key with the worm.
In the second phase, we connect our USB key on our test computer.
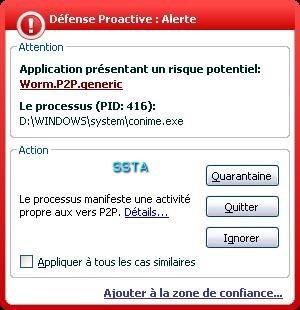
Kav does not block the autorun, and in this case the infection (F1)
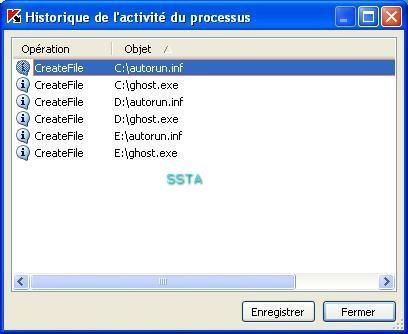
Windows has also prevention features (DEP):
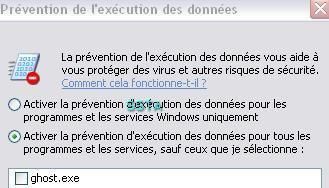
Too late...
On demand scan via right click:
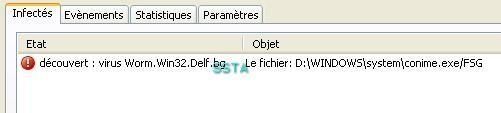
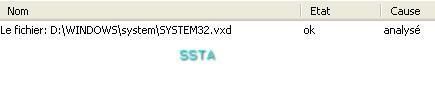
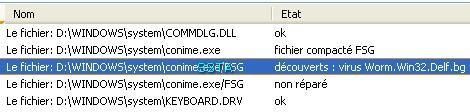
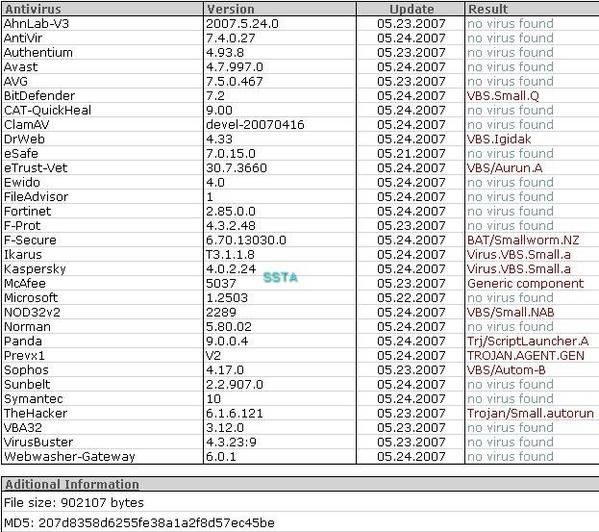
b) Virus VBS.Small.a: F1/P2
We definitively love McAfee terminology ("generic component")...
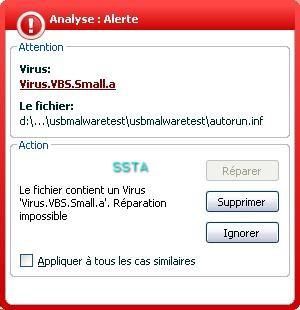
c) Unknown usb autorun malware: F1/F2
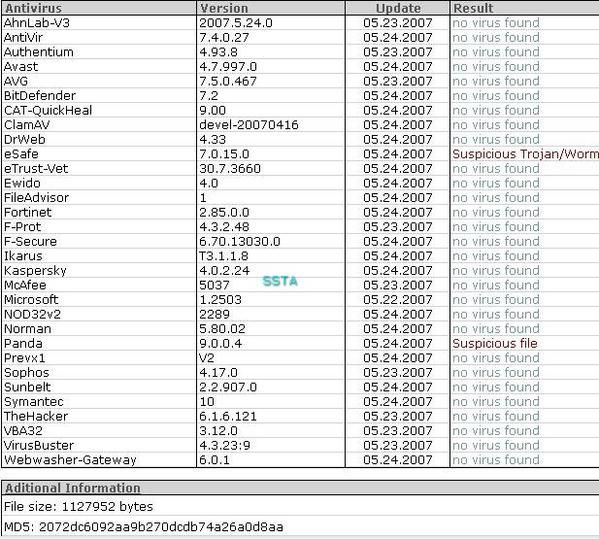
Here again, the song remains the same: "don't worry..."
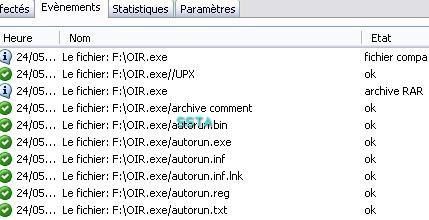
Here once the file run it reboot automatically the computer, after killing any running application (Kaspersky servive and gui included).
We did not done a full analysis (by hiddign the debugger for instance).
At the reboot, there is no access to C:
Fortunately the system is on D: partition.
If we right click on C, we have advertising for the malware coders..
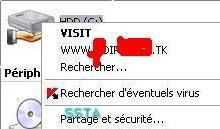
And we can't launch an on demand scan of C with Kaspersky scanner.
For a gain of time,we restore our clean test environement.
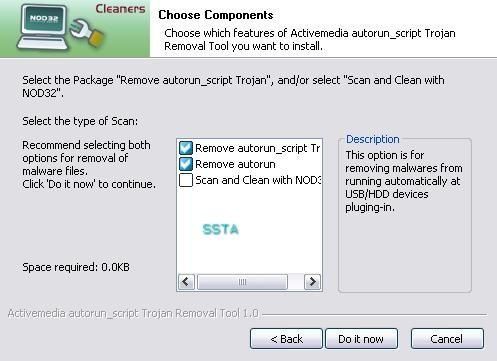
NB. We can mention the effort of the Nod32 " Thaï " team which has released a useful tool agaisnt this kind of threats related to autorun.
Nod32 autorun Fix Script helps to disable and remove autoruns malwares in particular, and works even if the user has an other antivirus installed (don't check the last option).