ROOTKIT TEST B Next
16) Trojan Downloader Win32.Small.emg/SpamBot variant:

We can't reproduce a real life situation for this test (the infection occurs via web sites), and we jus run the files locally.
Detection with Helios Lite and Spyware Process Detector (a clone of Security Task Manager) and two CMDLine hidden service detectors:
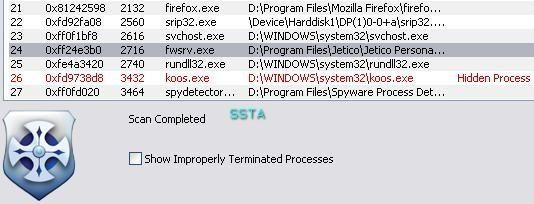
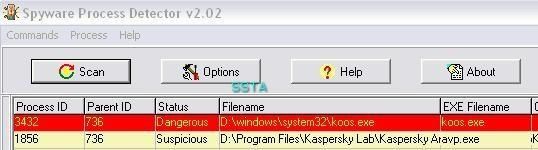
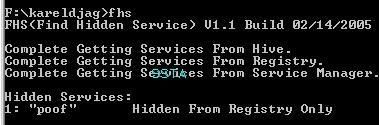

a) detection: P1/P2

b) prevention: P1/P2
A few screeshots in a non-particular order (the malware package includes several files):
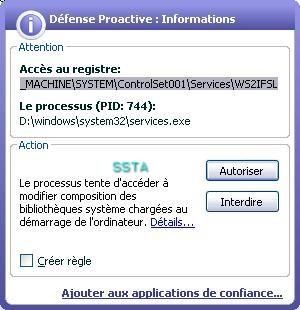
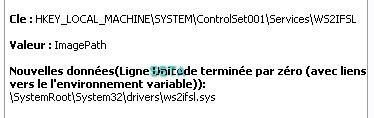
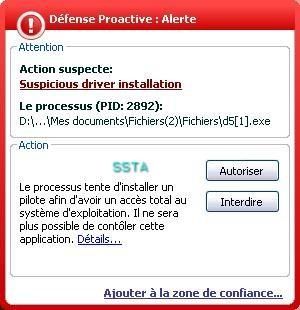
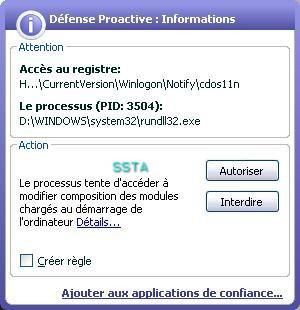
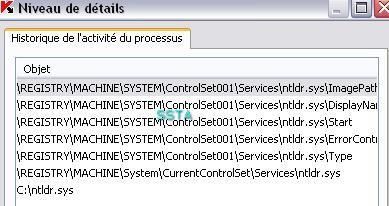
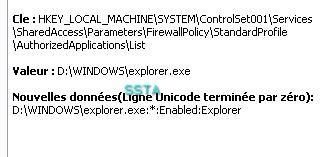
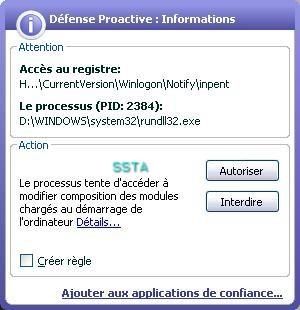

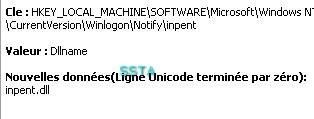


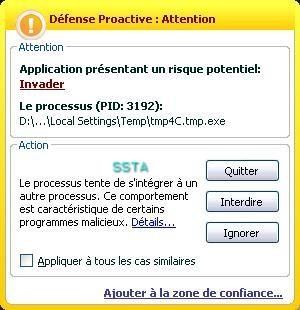

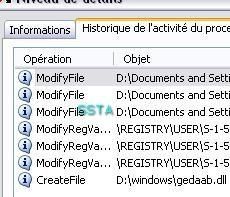
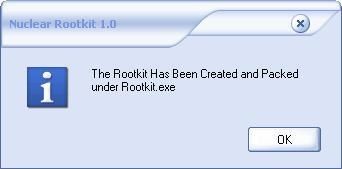
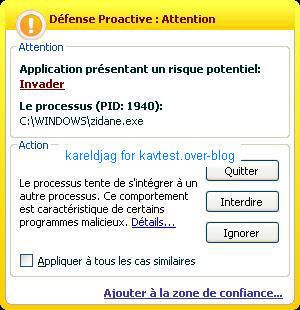
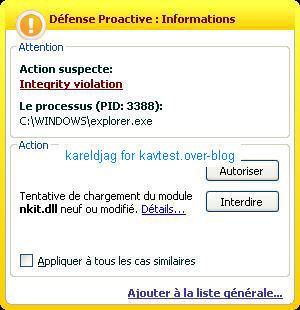
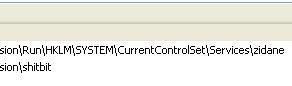
17) Nuclear Rootkit:
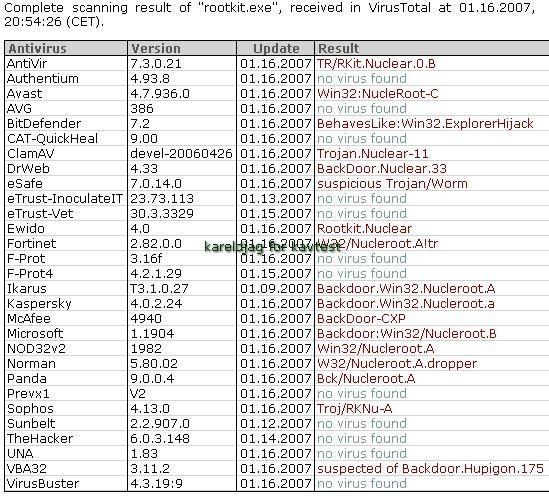
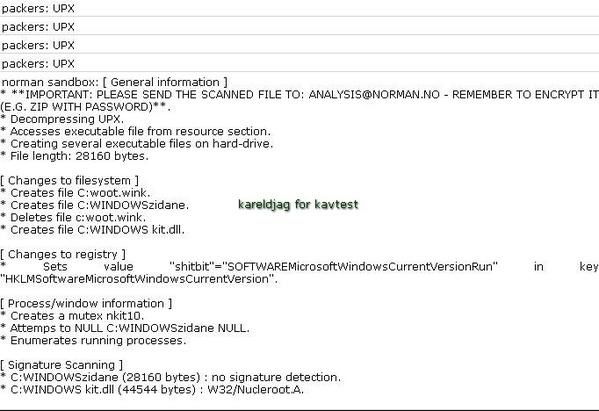
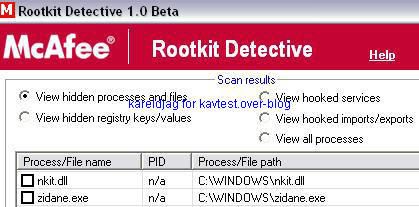
a) detection: F1/P2
b) prevention: P1/P2
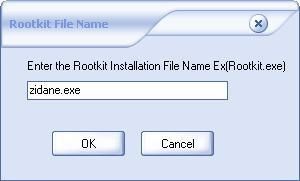
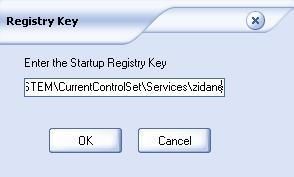
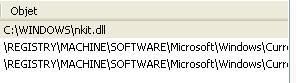
18) WinRootkit
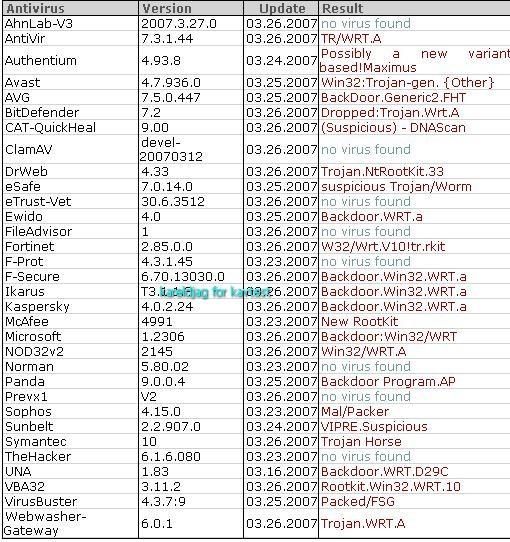
Detection by Seem, IceSword, SySprot and RKU:

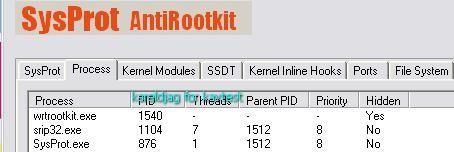
Same test launch from another drive (D):
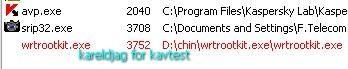

a) detection: P1/P2
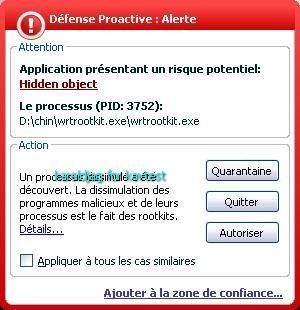
b) prevention: P1/P2
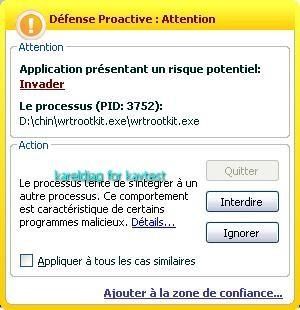
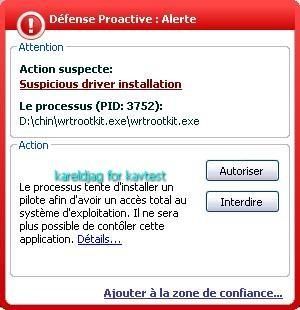
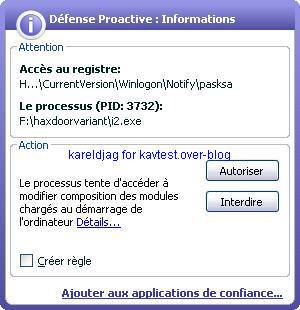
19) Haxdoor.cn
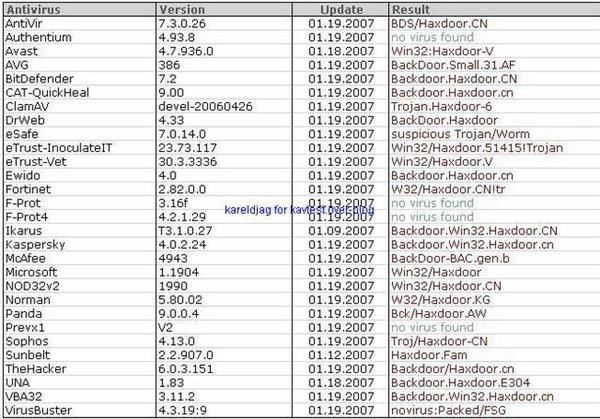
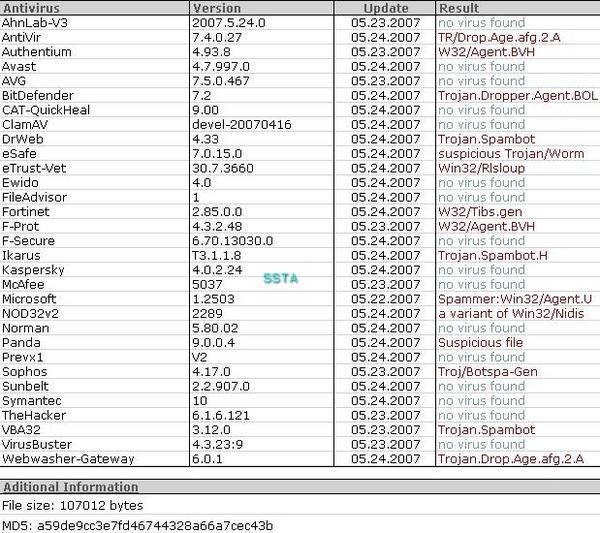
Detection with several anti-rootkits:

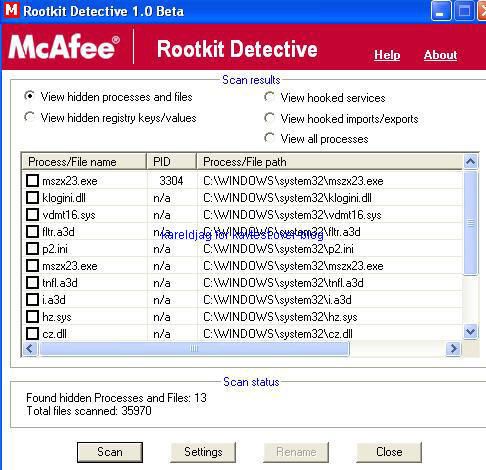
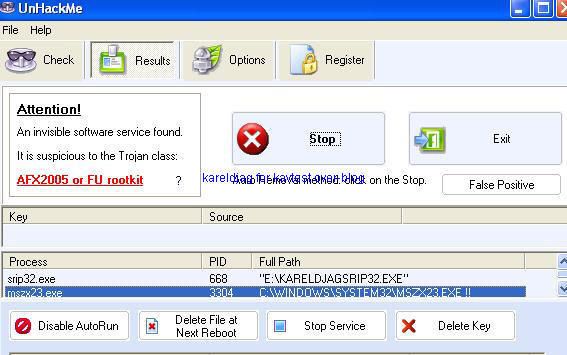

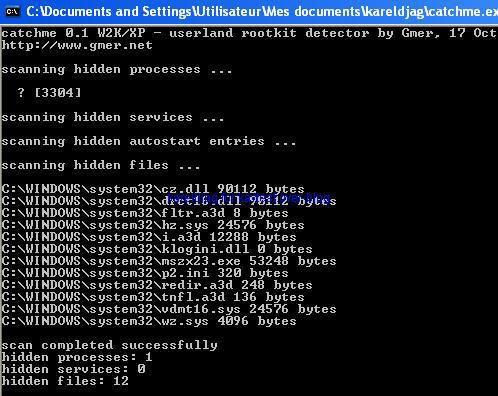


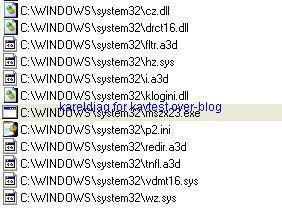
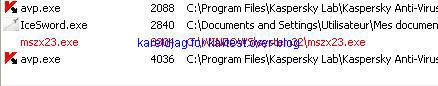
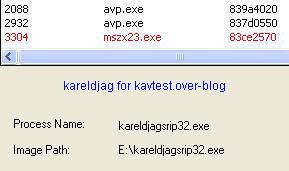
a) detection: P1/P2
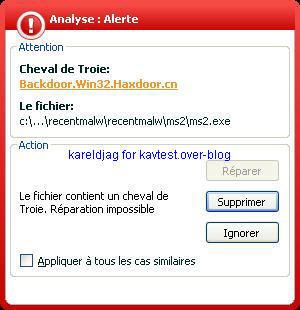
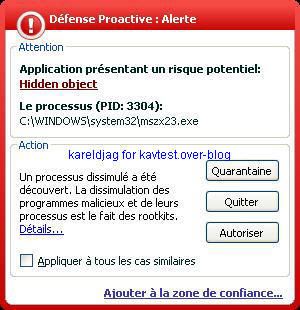
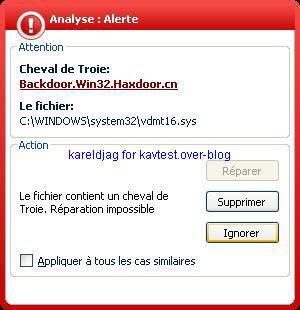
b) prevention: P1/P2
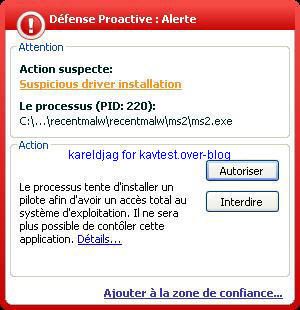
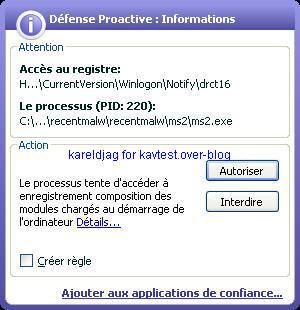
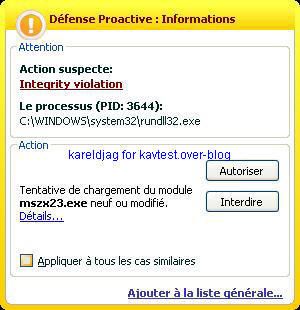
It's important to note that Kav prevents the rootkit from being permanent (service/driver and start up registry key can be blocked) but not the connection attempts:
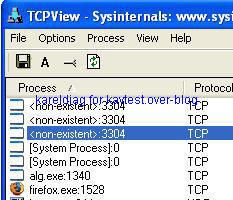
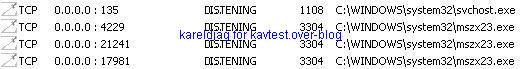
20) Rustock variant
Some analysis of Rustock and variant have already been published, but this one, published for the first HotBot conference is the most recent.
Here the log of NeovaGuard (free HIPS) on another test machine:

a) detection: P1/P2
b) prevention: P1/P2
21) Haxdoor variant (Haxdoor.ls)


a) detection: F1/P2 :
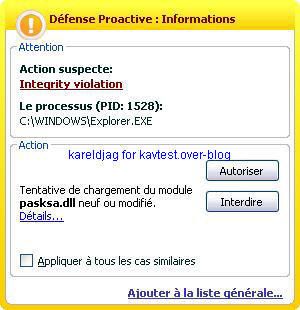
The hidden objects (.dll) are not reported as hidden by the proactive module, but the scanner engine can see and detect them as malicious (P2).
b) prevention: P1/P2
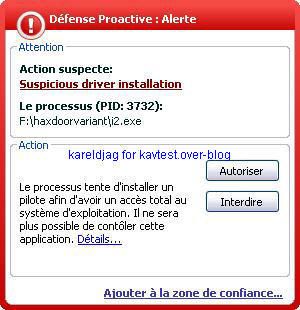

22) Trojan spy Turkojan

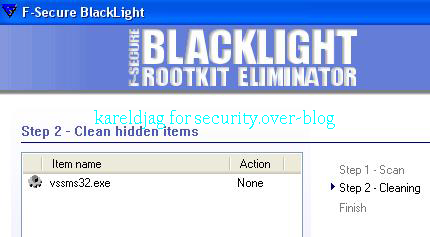
a) detection: F1/P2
b) prevention: P1/P2
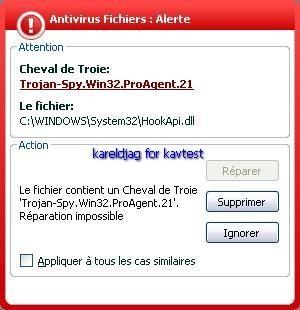
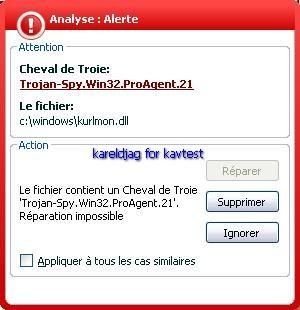
23) Trojan spy Proagent 2 :


Detection of Proagent hidden files with Rootkit Buster and McAfee Rootkit detective:


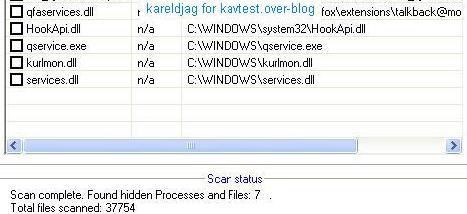
The hidden files are not detected by KAV (MST Net Framework and Mozilla tallback are not concerned by Progent).
a) detection: F1/P2
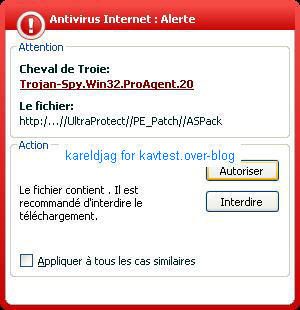
If the user launch an application (here the browser), kav warns the user about a dll injection (required to spy, basic and usual method):

b) prevention: P1/P2
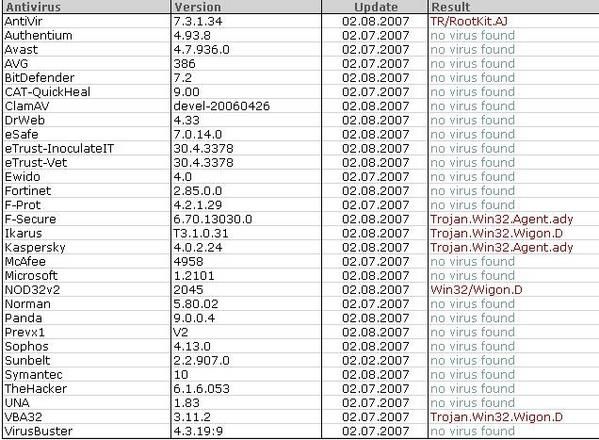
24) ProAgent variant (detected by most AVs on VirusTotal):
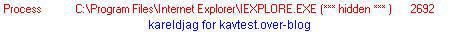

Fortunately, the malware is not designed to bypass the firewall (we have not set "allow always" rule for browsers, which is a paranoiac firewall configuration):
The dll injection and global hooks (keylogging) is here detected by good firewalls like Comodo:
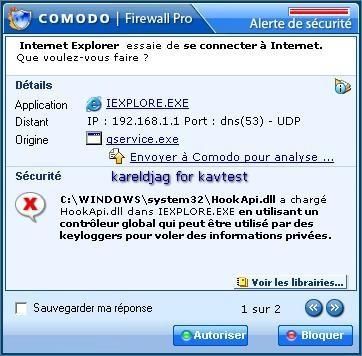
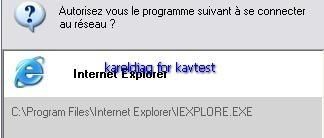
a) detection: F1/P2

Critical object scan:
b) Prevention: P1/P2

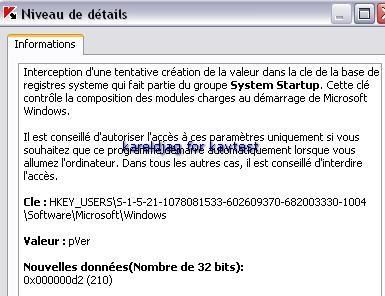
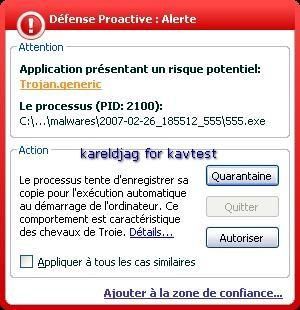
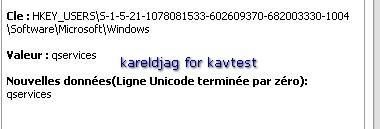
25) Wingon rootkit:
a) detection: P1/P2
b) prevention: P1/P2

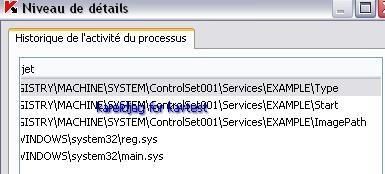


26) Winrootkit chinese variant:
a) detection: P1/P2
2) prevention: P1/P2
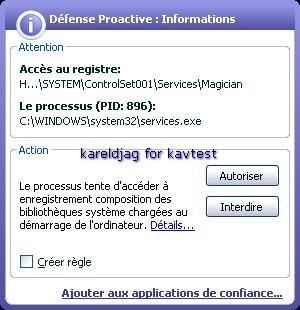
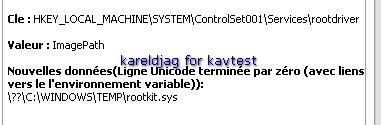
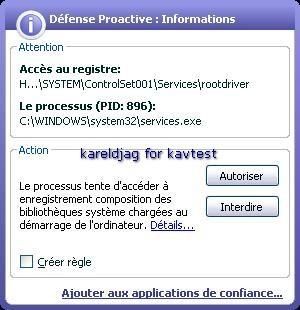
27) Haxdoor variant (.jw):
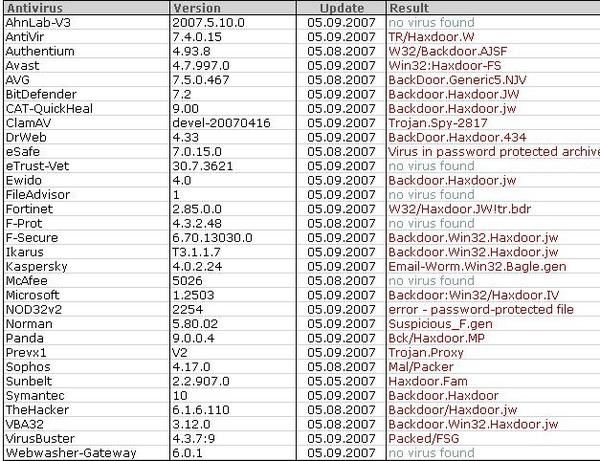
Detection via IceSword:
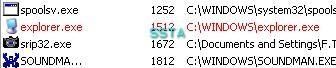
a) detection : P1/P2
b) prevention: P1/P2
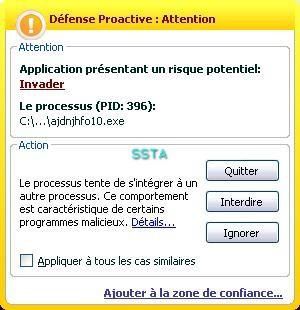

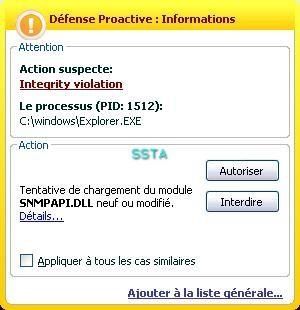
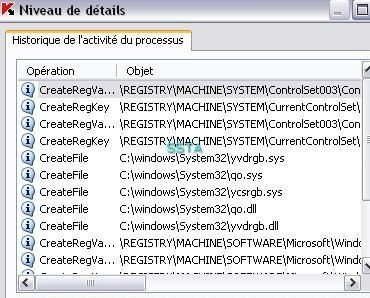
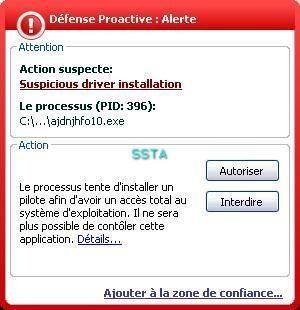

28) Oddysee version 2

We choose to hide a classical backdoor (NetCat).
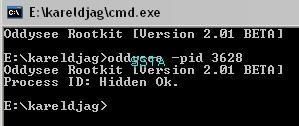
Detection by IceSword:
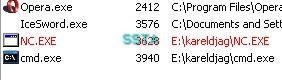
And by TrustDefender (HIPS based anti-phishing):
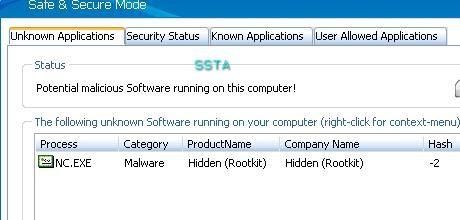
a) detection: P1/P2
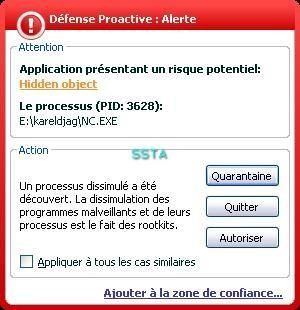
b) prevention: P1/P2
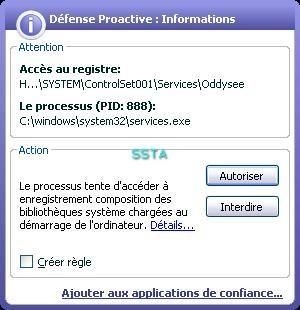
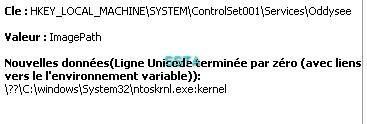
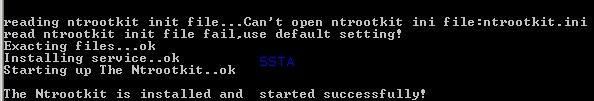
29) NTRootkit:
This is here an excellent illustration of classical rootkit (intruder/hacker tool): this rootkit can work with Netcat, and provides various extra features and options for the remote attacker (in this test, we just install the rootkit).
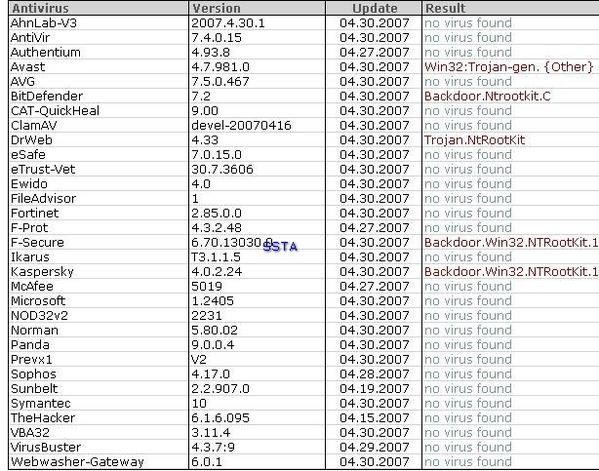
Option available once connected to the rootkit (use of ICMP packets to bypass port mappers and firewalls, DDOS command etc):
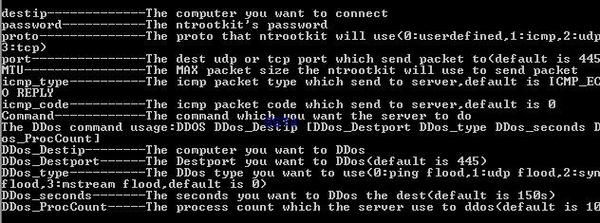
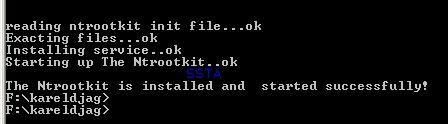
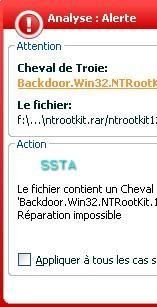
Detection by various tools and Anti-Rootkits softs:
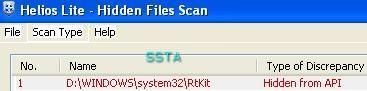

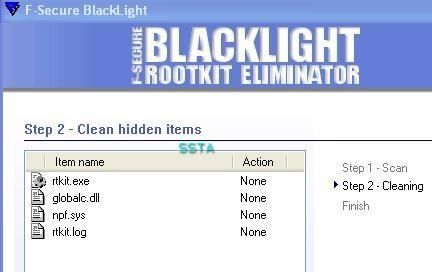
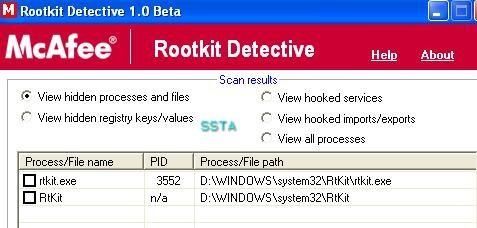
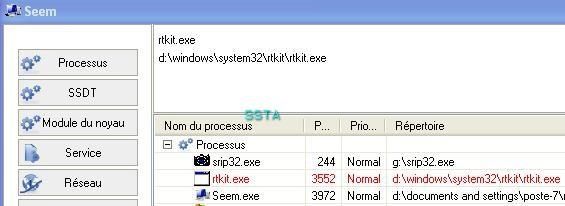
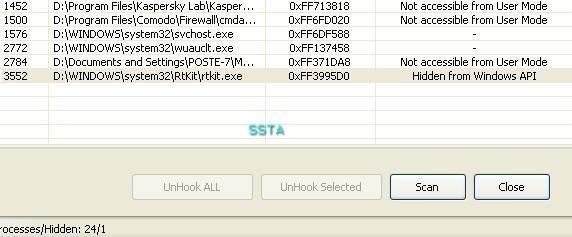

If we list running process with process dumper, we can see that rtkit.exe is not displayed:
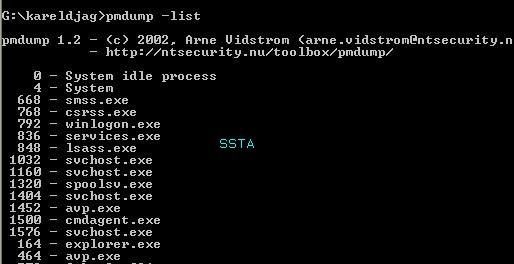
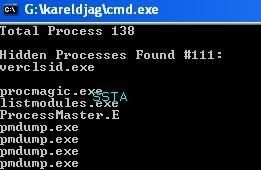
We need more: ProcessMaster? not enough:

Process Magic? Not really reliable...
Better with Catchme (or ProcessWalker) and hidden service detectors:
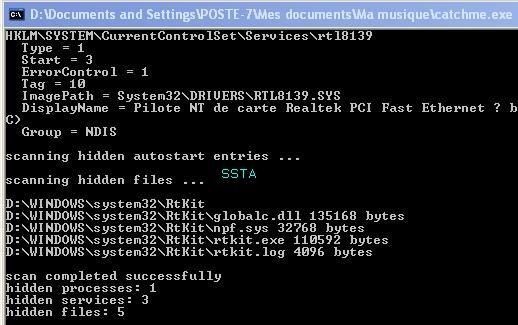

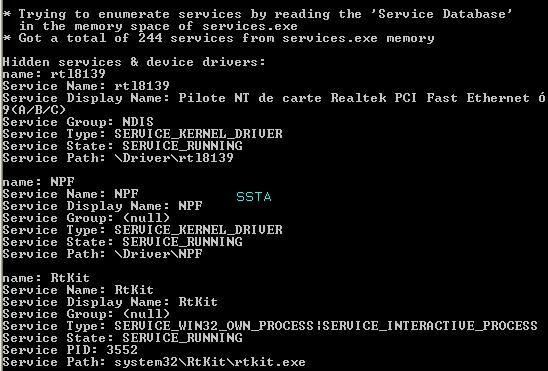
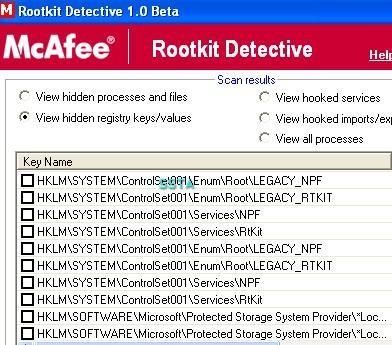
If we dump important HKLMSYSTEM keys used by rootkits:
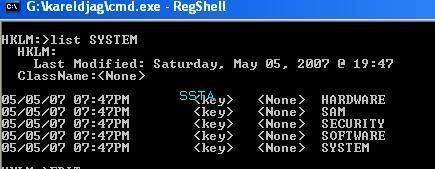
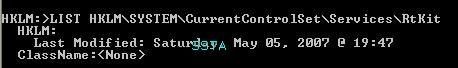
Let's check if the key is hidden or not:
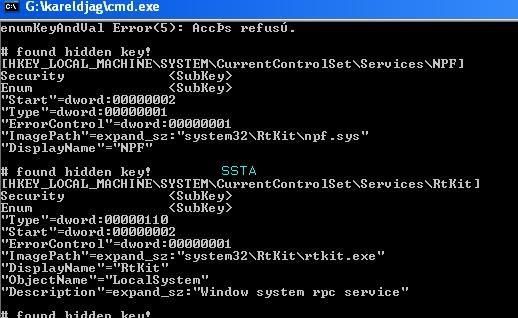
a) detection: P1/P2

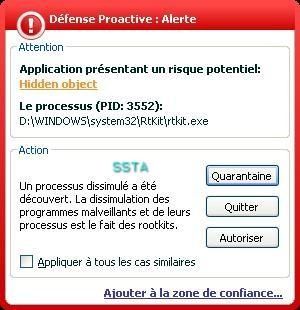
b) prevention: P1/P2
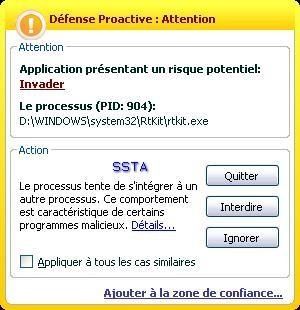
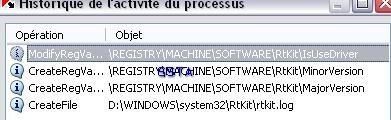

The rootkit is blocked (servicedriver installation) even if the next image displays that the rootkit is running!