WORMS, VIRUSES AND SCRIPTS 3
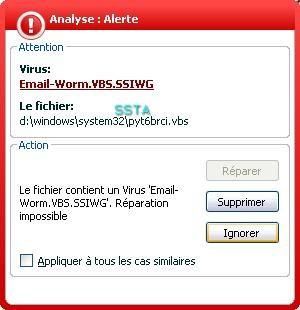
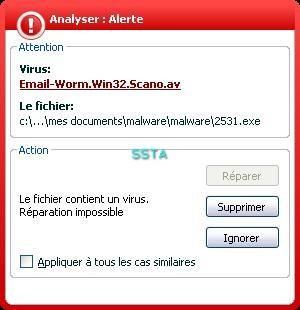
-Worm Scanao: P1/P2
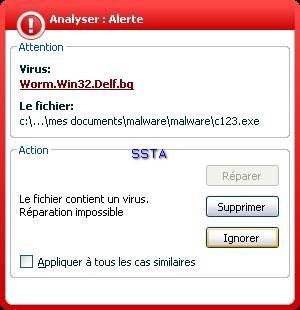
-Worm Delf.bg (also knwon as Worm Cekar by sophos): F1/P2
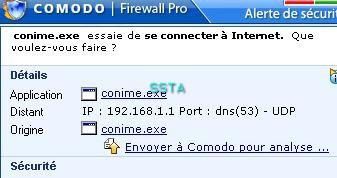
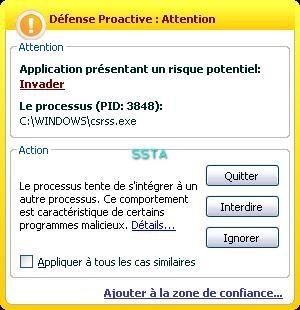
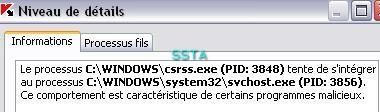
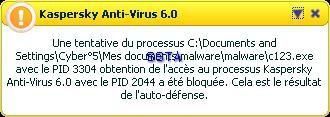
Kav self-defense:
When the host is already infected, the PDM detects s suspicious behaviour, but it's too late (no prevention).
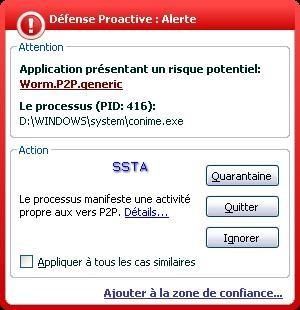
-Worm Locksky.au: P1/P2
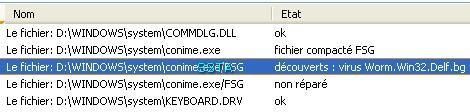
-Worm Jalabed.b: P1/P2
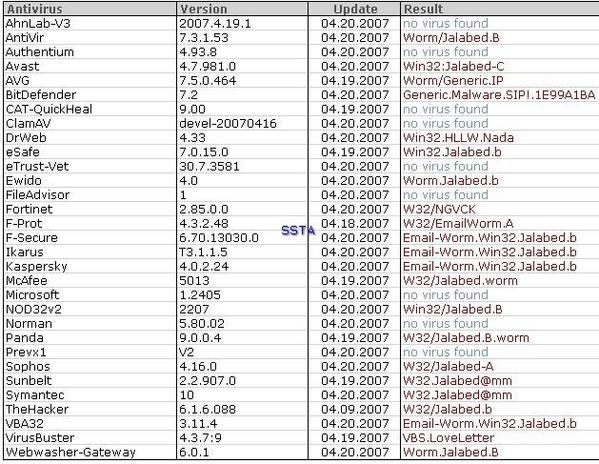
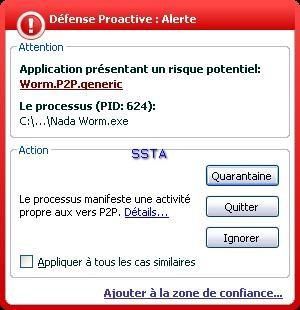
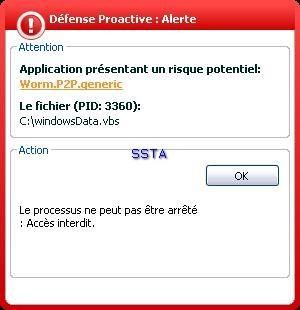
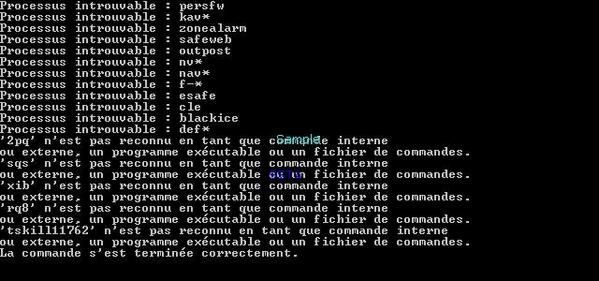
Worm with an exhaustive list of security software processes to kill:
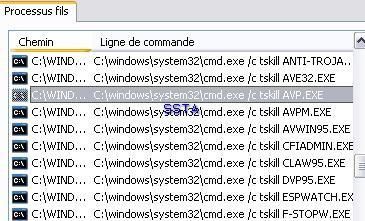
As it is shown on the next image, a command is sent in order to kill Kav (avp.exe):
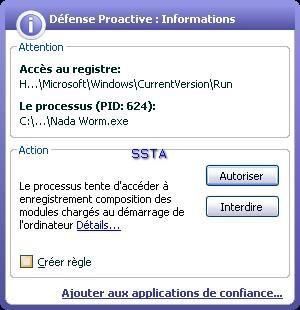
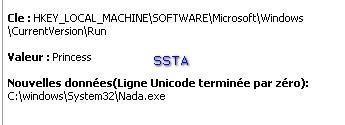
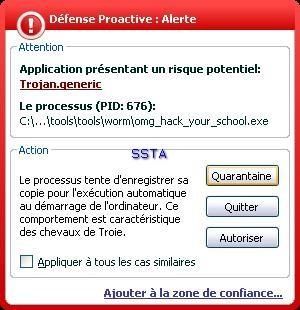
-Generated Virus" (by a malware generator) :P1/P2
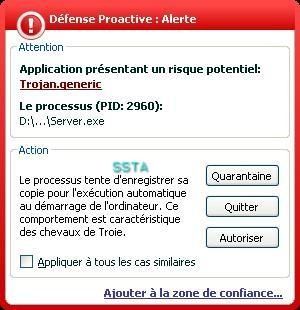
-AutoExe worm (no AV editor has the right name, so we keep the original file name): P1/P2
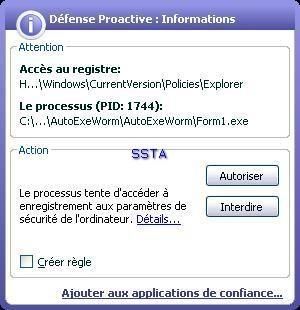
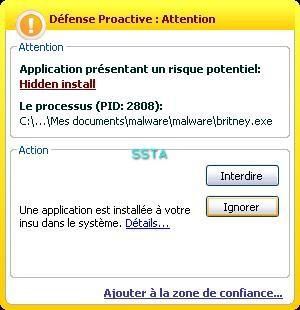
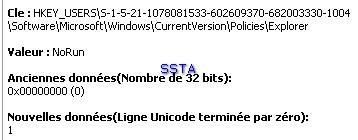
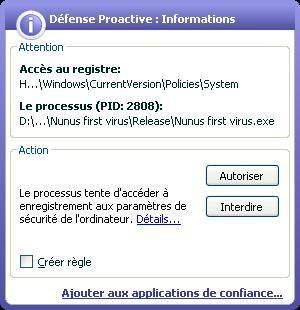
A nasty run key: the user will not find his desktop at the reboot...if he clicks on the allow (Autoriser) button.
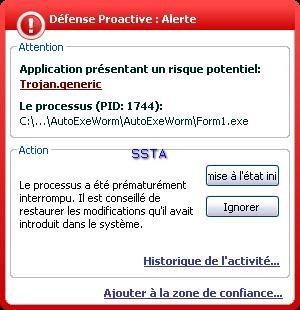
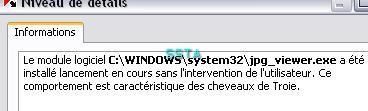
The file is not known from kav malwares database, another illustration of the need of a an HIPS/proactive module.
Here again: unseen by the antivirus file protection, catched by the PDM.
-Worm Banwarum.f: F1/P2
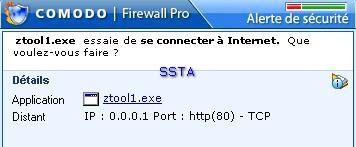
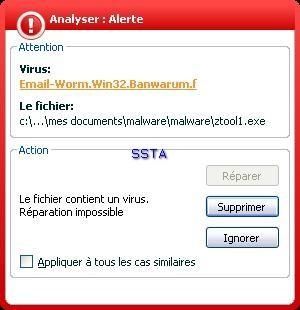
-Worm Small.m (the right classification is given by BitDefender, but we keep the Kav's terminology and classifiction): P1/P2
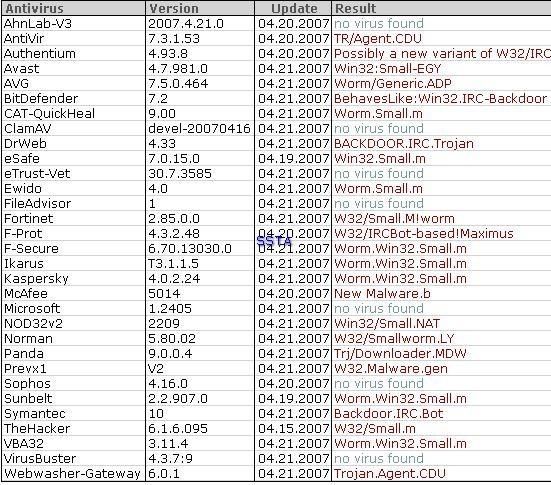
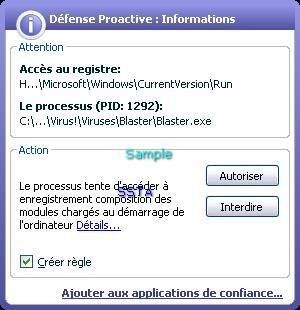
-Blaster: P1/P2
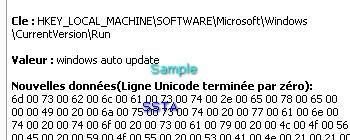
-Antimarketing virus: F1/P2
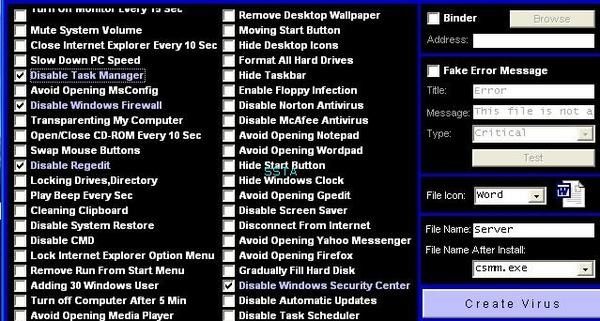
For this example, we use a virus generator: we create a destructive virus that we call "antimarketingvirus" :
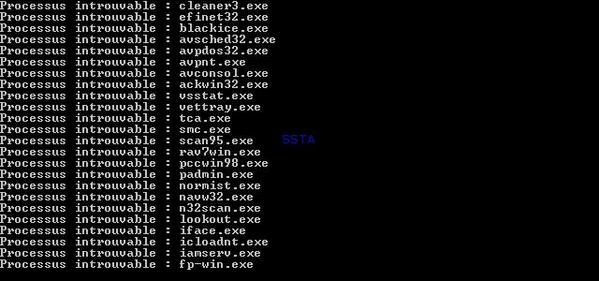
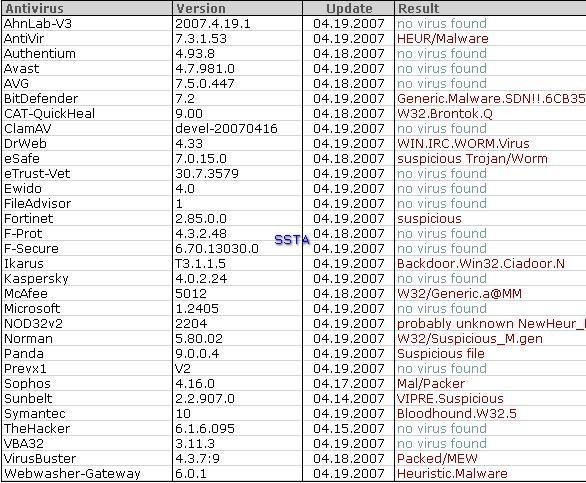
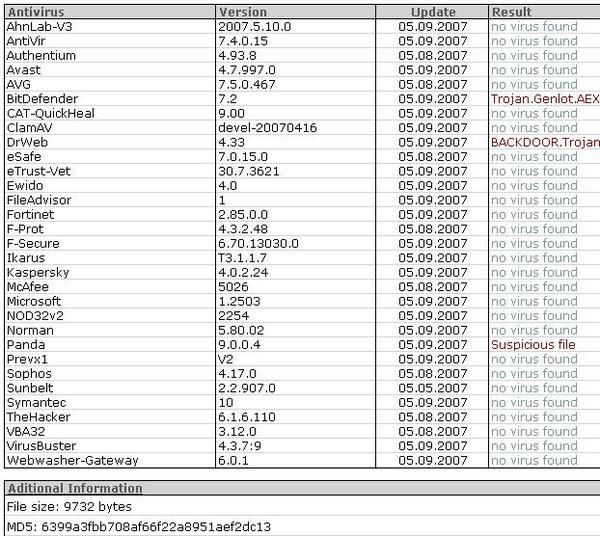
Let's see which scanners (heuristic) are sleeping and which are wake up:
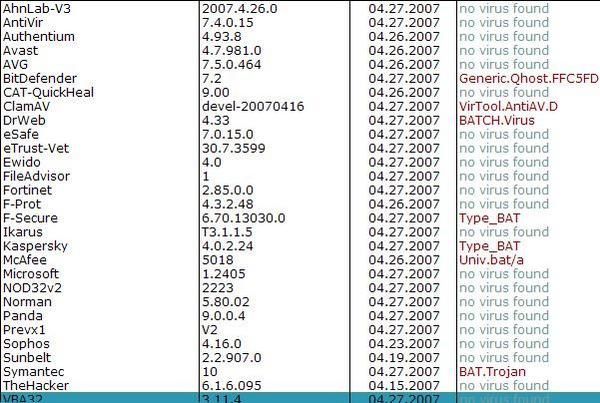
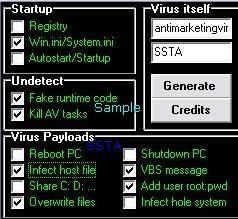
The virus searchs for known security process in order to kill them:
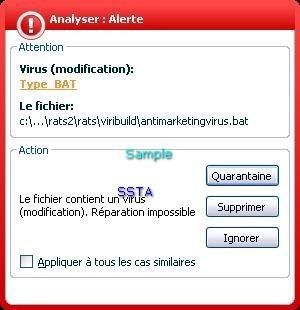
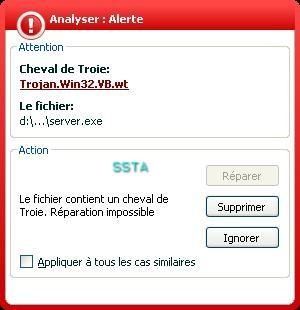
F1: Kav has not detected the deletion of files.
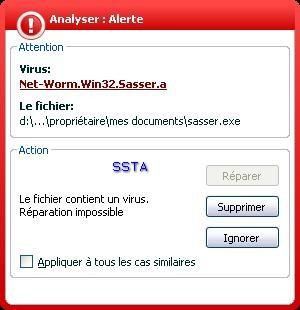
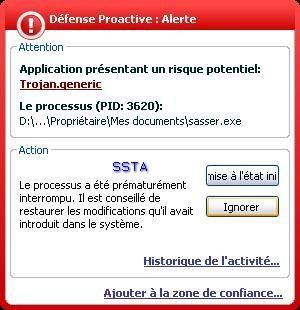
-Sasser: P1/P2
-Nunus virus: P1/P2
A simple anoyance virus.

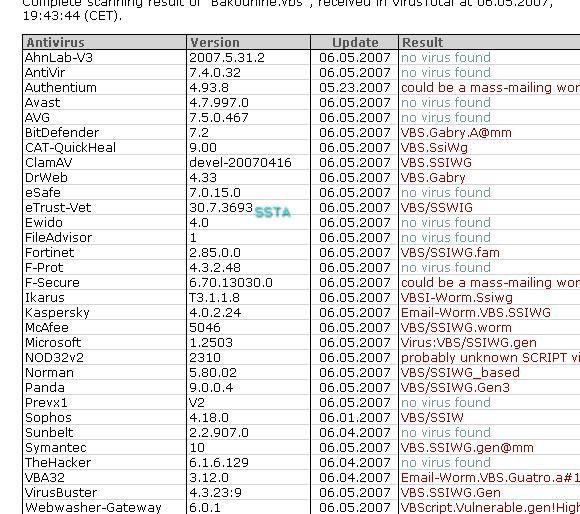
-Generated worm: P1/P2
Here we use a tool which generates malicious scripts: the goal here is alos to test the heuristic engine.
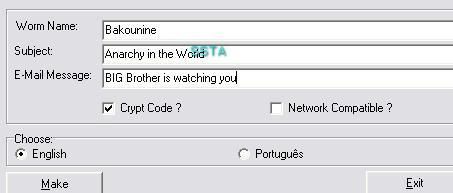
We create a vb script that we call Bakounine (we use the french name):
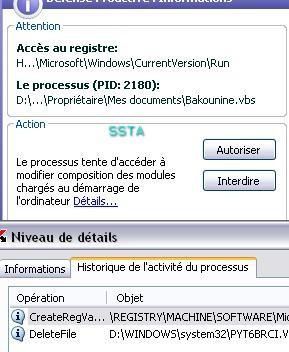

The scanner has done its job: