OTHER MALWARES Part 5
-Bdoor backdoor: P1/P2
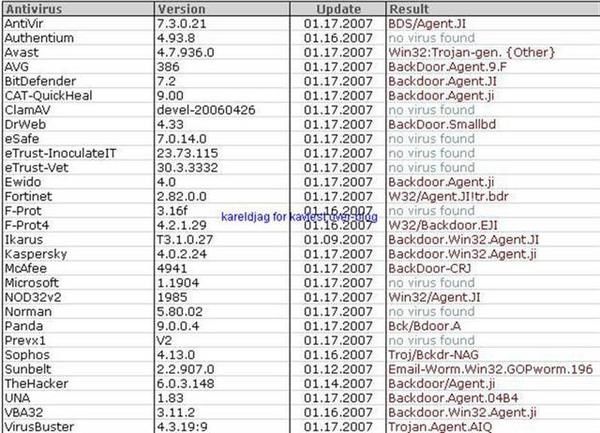
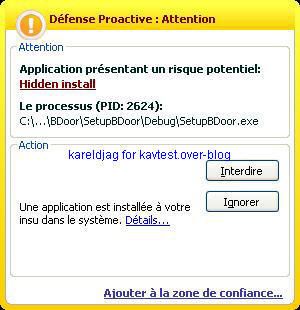
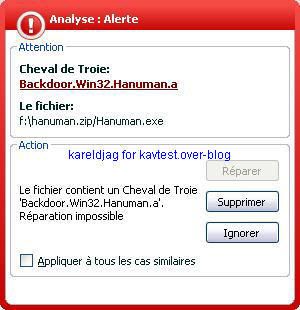
-Hanuman Backdoor: F1/P2
This backdoor does not try to be permanent by wrinting the run key (F1):
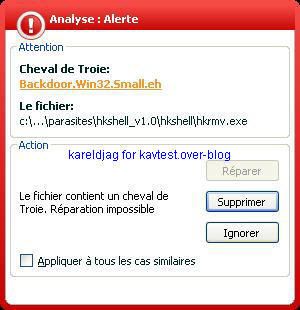
-HKShell backdoor: P1/P2
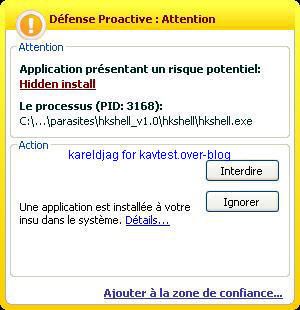
-ICMPDoor backdoor: P1/P2
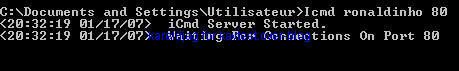
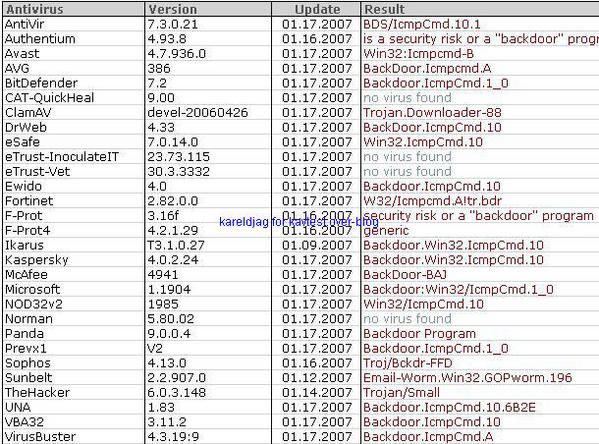

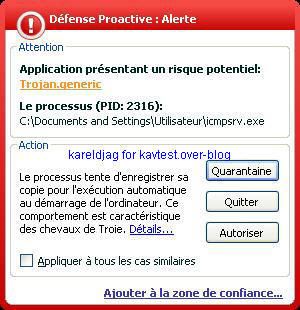
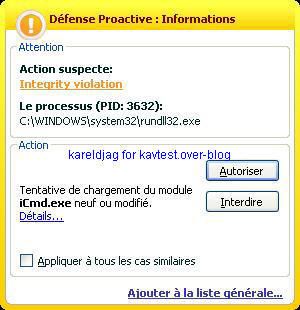
NB. ICMP is consdered as a "poor protocol", but it is certainly one of the most interesting for firewall and IDS evasion.
This protocol is for instance used by some malwares for data leak.
-HTTP Rat Zombam: P1/P2

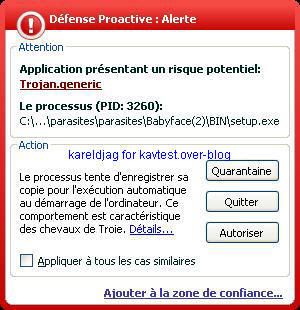
-BabyFace trojan: P1/P2
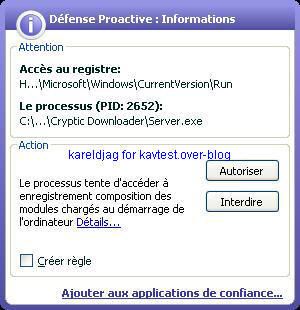
-Scryptic downloader: P1/P2
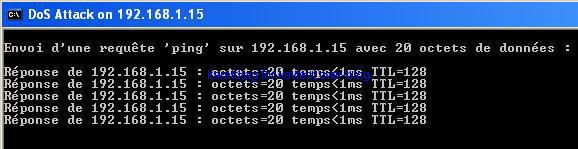
-ICMP DDOS Tool: F1/F2
This test is designed to show if kav can prevent network attack from being started (when the host is a part of a botnet for instance).
-Letmerule backdoor: P1/P2

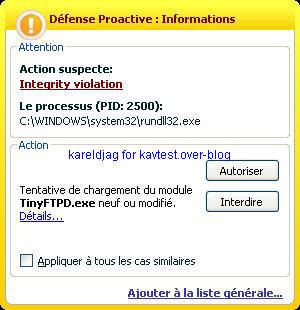
-Tiny FTP backdoor: P1/P2
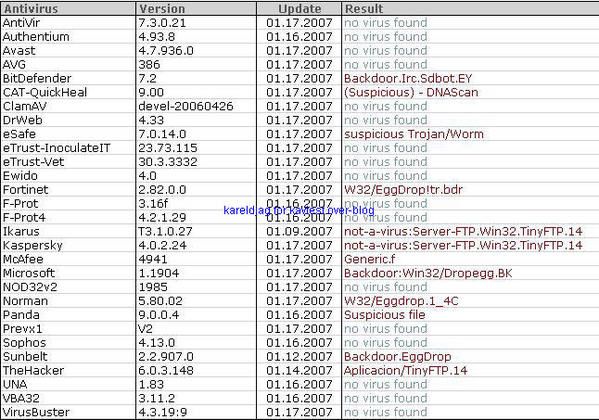
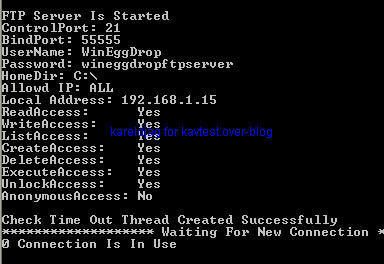
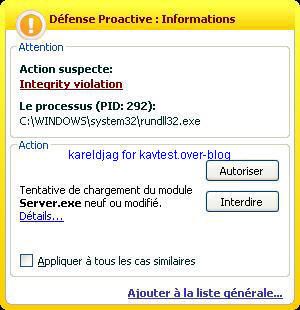
-Backdoor Sensode/ZXShell (a kind of NetCat variant): P1/P2
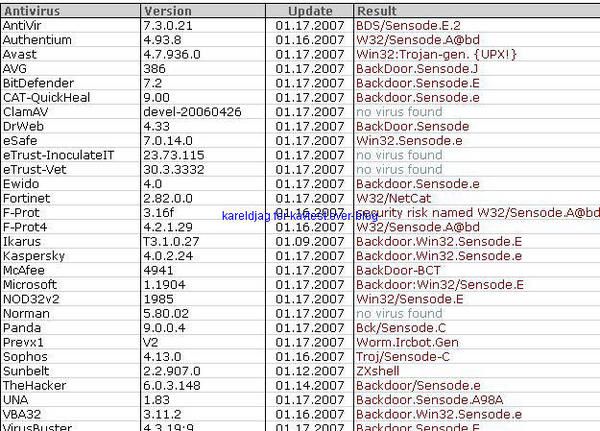

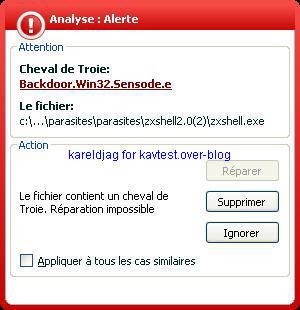

Unfortunately, the deny answer does not prevent the connection attempt:
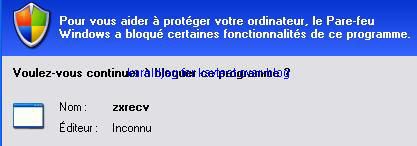
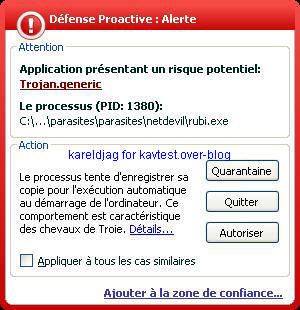
-NetDevil backdoor: P1/P2

-Nuclear RAT: P1/P2
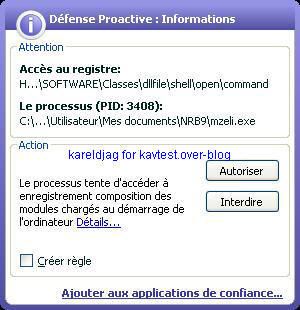
-Roxrat backdoor: P1/P2
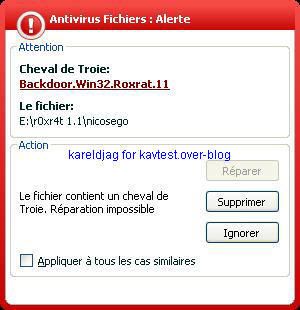

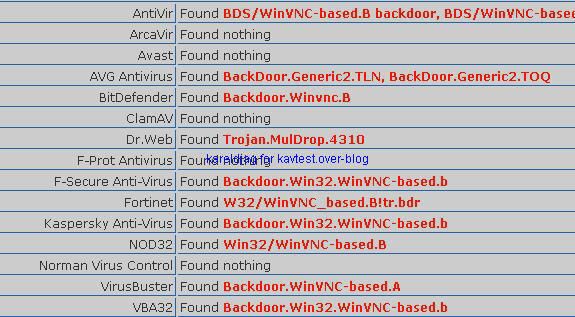
-WinVNC backdoor: P1/P2

-Oblivion backdoor: F1/P2
NB: we have not enable the creation of a run key for the server.
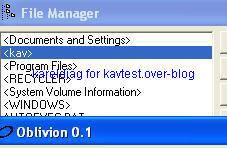
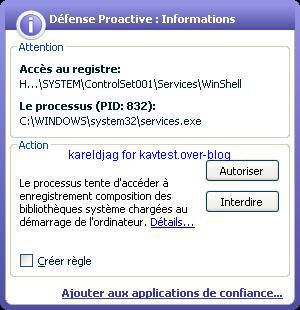
-Winshell backdoor: P1/P2
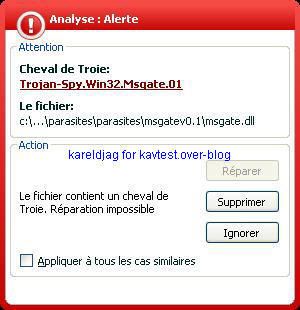
-Msgate Trojan spy: P1/P2

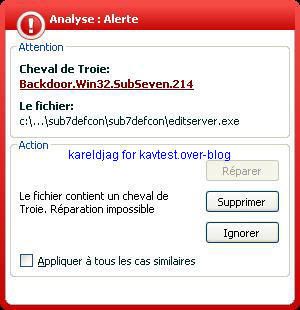
-Sub7 variant: P1/P2
-PHP backdoor: F1/P2
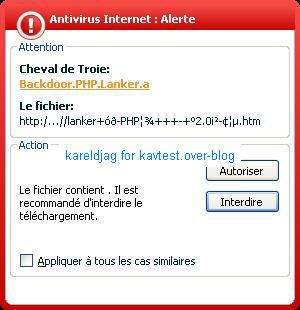

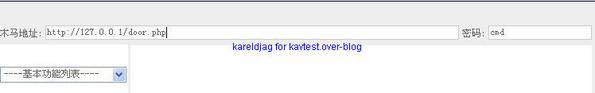

-So2Rat backdoor: F1/F2
We can run the server and connect to it without any kind of alert from the proactive module, neither from the antivirus file (malware unknown from kav labs).
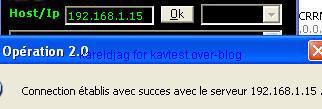
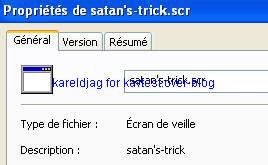
-Satan's Trick trojan dropper: P1/P2
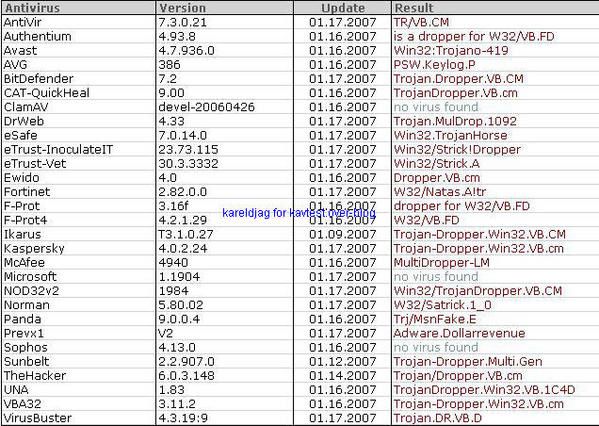
The test file version looks for the victim as an innocnet screesaver:
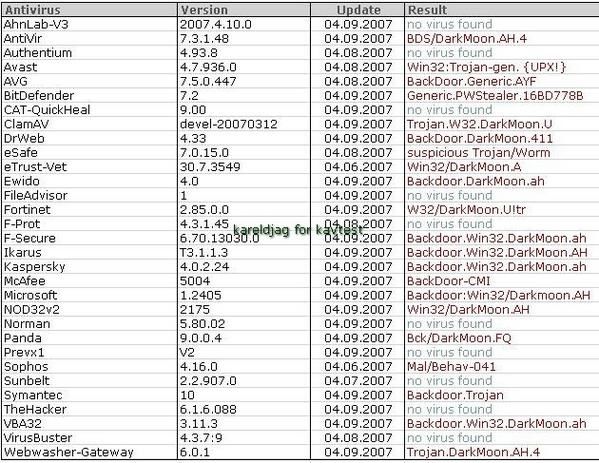
-DarkMoon trojan: P1/P2
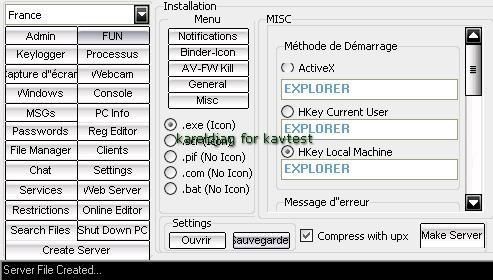
We choose to create a server that we call pornflashgame.exe...a very attarctive kind of games for men...



